Covenant
Installation
Install Dotnet
cd /tmp
wget https://packages.microsoft.com/config/ubuntu/21.04/packages-microsoft-prod.deb -O packages-microsoft-prod.deb
sudo dpkg -i packages-microsoft-prod.deb
sudo apt update -y
sudo apt-get install -y apt-transport-https dnsutils
sudo apt-get update
sudo apt-get install -y dotnet-sdk-3.1 Install and launch Covenant
sudo git clone --recurse-submodules https://github.com/ZeroPointSecurity/Covenant.git /opt/Covenant
cd /opt/Covenant/Covenant
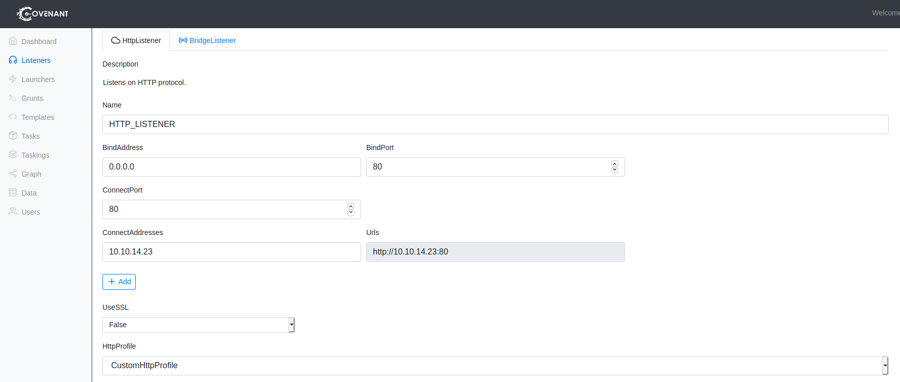
sudo dotnet runStart a listener
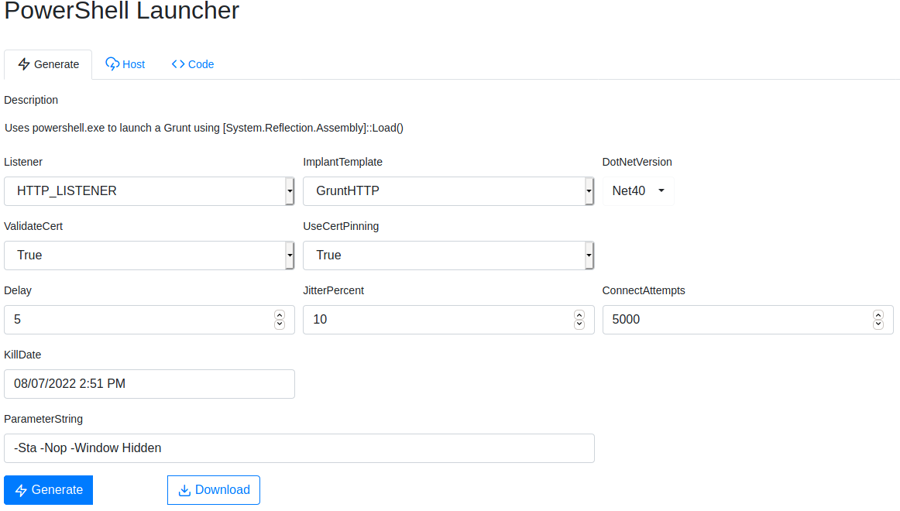
Create a Launcher to get a shell
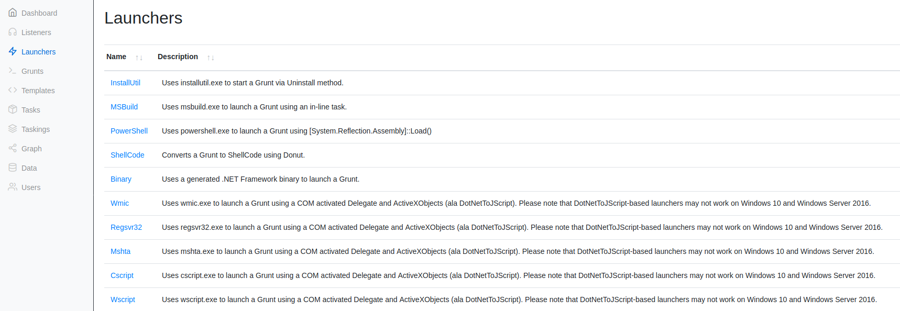
Launchers type
Local Enumeration
hta Email Phishing
- NameListenerTypeStatusStartTimeConnectAddressesConnectPort
Dump hashes with mimikatz
Cracking Credential Vault with mimikatz
Common issues with Covenant
Resources
Last updated