Hackthebox - BackendTwo
Linux

Nmap
Port 80
Gobuster

Just like with the first backend box we can enumerate users with the id

http://10.10.11.162/api/v1/admin/requires authenticationhttp://10.10.11.162/docsrequires auth
Wfuzz
Let's fuzz with wfuzz and http verbs to see what we could do
We are able to create a user (same process as the previous backend box)

We can now login using the user and we get a bearer token

Then we can access the swager with intercept on we add our token bearer and set the cntent type to json

We get redirected to openapi.json

We have a user flag request in the swagger let's try to grab it
we need to be admin to grab it
Also we can enumerate users with burp intruder

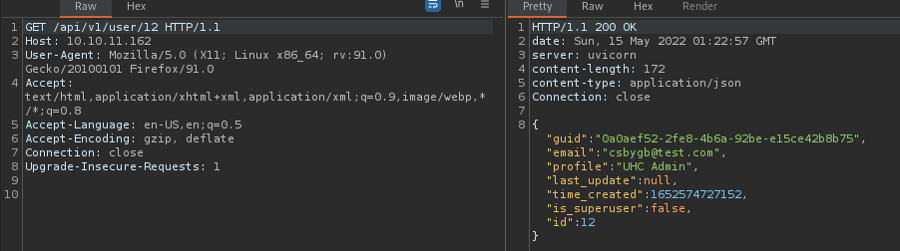
We get 11 users + 1 (the one we created)
We are also able to see other profile we are player:
"profile":"UHC Player", there is also a guest"profile":"UHC Guest",and of course the Admin (the first one we found)In the swagger we can actually edit a profile. Let's try to make ourselves admin. It works!

If we check we are indeed admin
However we can see that we are not super, let's try to put ourselves the is super user to true with the put request to edit

And it worked too

We have to login again and generate a new token, let's replay our initial login request

Let's try to grab the flag again with this new token. It works

Let's now play with the read file and write file request we can see in the swagger to get a file the name needs to be in base64 url as mentioned in the swagger
We are able to get /etc/passwd this way

Let's try to get the main.py it should be here
/home/htb/app/main.py
We can not write file because it is asking for a debug key (just like the first backend box)
This line in the main.py app could help us
app.core.config import settingsLet's try to see
/home/htb/app/core/config.py
we apply changes and fetch it

And we see in the settings that it gets it's secret from an env var
JWT_SECRET: str = os.environ['API_KEY']We need to get the
/proc/self/environ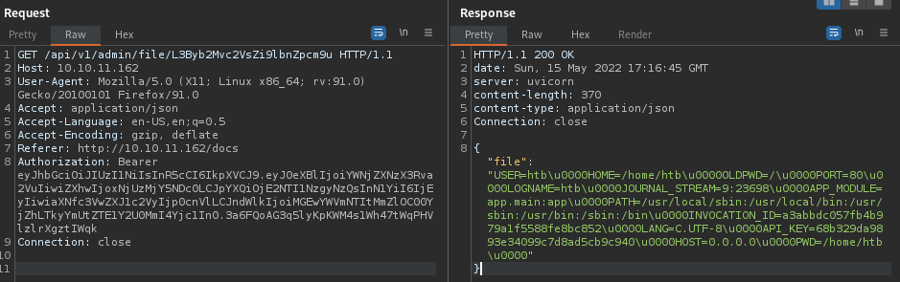
We have the private key:
API_KEY=68b329da9893e34099c7d8ad5cb9c940Now we just need to modify our token on jwt.io with the private key and add the debug to true. Let's take the token and paste it in there and make the changes

It works!

At this point we could try to overwrite a script in order to make an endpoint to send a reverse shell
Let's fetch user.py (we can use ippsec's script from the bonus section below to fetch it)
./getfile.sh app/api/v1/endpoints/user.py > user.pyWe can add this in the end of user.py:
Now we have to take the whole script and escape it in json we can do this with this website and we get our new script:
We save it in a file named escaped
now we can use it in a new bash script (I named it exploit.sh)
now we launched it

Now if we refresh our swagger (/docs) we see a new method

Let's set a listener on the port we specified in our script (4444)
rlwrap nc -lvnp 4444Let's try the new method. We get our shell

Privesc
We can cat the auth.log we see a password

Turns out it is the htb user password not the root so in case we need to ssh as htb we have a password
1qaz2wsx_htb!if we sudo -l with the user it launches a wordle game

It was good that we kept the password because I lost the shell so I could ssh back into it
Let's try to find the script that uses wordle
find / -name *wordle* 2>/dev/null
Let's make a string on the file
strings /usr/lib/x86_64-linux-gnu/security/pam_wordle.soThis file seems interesting
/opt/.words
These are all the guess words
We can use the list to cheat
Let's copy it and paste it in a file
Now we just need to launch the game again with sudo -l
So the word has an m somewhere else so let's find a word with another m
So now we have an m an o and a c except the m is not in the begining and not in 4th place let's launch another shell and grep on our file with all the words. Here is what we get:
 A the m is not at the begining of the word it let's try
A the m is not at the begining of the word it let's try chmod, it works
 And we can run all the commands so let's just grab the flag with cat
And we can run all the commands so let's just grab the flag with cat sudo cat /root/root.txt
Bonus
If you do not want to manually fetch the file with burp you can use this script from ippsec's video writeup (see link in resource), it will fetch the files without the annoying chars by using tr
Resources
Last updated