Information Gathering
Physical / Social
Web / Host
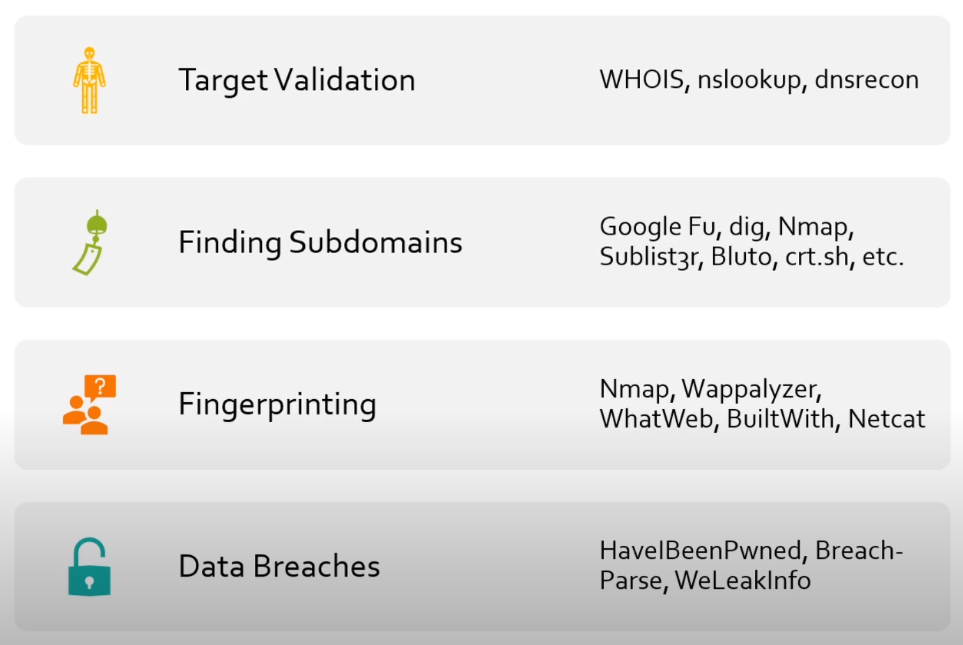
Identifying our target
Discovering email address
Gathering breached credentials
Web information Gathering
Using search engines
Using Social Media
Tools
Last updated