Scanning & Enumeration
AKA Vulnerability Assessment. In this step we use the information found to identify potential weaknesses. We can use vulnerability scanners that will scan the target systems for known vulnerabilities and manual analysis where we try to look behind the scenes to discover where the potential vulnerabilities might lie. Time, patience, and personal commitment all play a significant role in information gathering. This is when many penetration testers tend to jump straight into exploiting a potential vulnerability. This often fails and can lead, among other things, to a significant loss of time. Before attempting to exploit anything, we should have completed thorough information gathering, keeping detailed notes along the way, focusing on things to hone in on once we get to the exploitation stage. Most assessments are time-based, so we don't want to waste time bouncing around, which could lead to us missing something critical. Organization and patience are vital while being as thorough as possible. In other terms, we analyze the results from our Information Gathering stage, looking for known vulnerabilities in the systems, applications, and various versions of each to discover possible attack vectors. Vulnerability assessment is the evaluation of potential vulnerabilities, both manually and through automated means. This is used to determine the threat level and the susceptibility of a company's network infrastructure to cyber-attacks. Source Hackthebox Academy
The machine used in the lab here for the example is Kioptrix from vulnhub
During this stage it is really important to take good notes. We have to write versions we find any information disclosed during this phase.
Scanning with nmap
Identify all the machines in a network
netdiscover -r 10.0.2.0/24
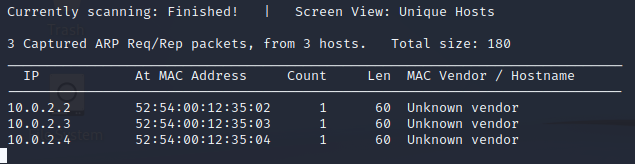
Scan with Nmap
nmap -Pn -sV -sC -p- 10.0.2.80my fav scan options (if I do not need to be stealthy)We can use the
-sSflag it is suppose to be stealthy (it is much more picked up today than it used to be). It is called stealthy because it is going to send SYN and when it will receive the SYNACK it will send a RST instead of an ACK (it means that when the remote machine is going to say "I am open you can connect" it is going to send something like "I do not want to connect anymore")nmap -T4 -p- -A 10.0.2.4nmap -sU -T4 -p 10.0.2.4In case we want to scan udp it is better to make a scan similar to this one because udp takes a long time to scan
Result
Here is the result from our example
Enumeration
Next step is to enumerate the services and protocols that showed up in our nmap scan. It is really important to take detailed not during this process. For more info about this checkout the networking chapter of my pentips. You will find steps for multiple protocols and services.
Questions to ask ourselves during enumeration
What can we see?
What reasons can we have for seeing it?
What image does what we see create for us?
What do we gain from it?
How can we use it?
What can we not see?
What reasons can there be that we do not see?
What image results for us from what we do not see? Source Hackthebox Academy
Principles
1.
There is more than meets the eye. Consider all points of view.
2.
Distinguish between what we see and what we do not see.
3.
There are always ways to gain more information. Understand the target.
Source Hackthebox Academy
Research
After this enumeration we can look up things we wrote down in our notes (vulnerable versions, vulnerable services, misconfigurations,...).
Search Engines
Usually we can try to google
technology version exploitfor examplemod_ssl 2.8.4 exploitIf anything shows up we can add it in our notes along with link to exploits to try them out later
searchsploit
sudo apt install exploitdb -yto installOn kali we can use searchsploit
searchsploit technology partial-versionfor examplesearchsploit Samba 2orsearchsploit SambaExample
searchsploit drupal 7.54You will then get a list of exploits or Metasploit modules

To download an exploit you then just need to do
searchsploit -m 46459 .with:46459name of the exploit (here we took the last one from the screen above).the path to the folder you want to copy it to

Vulnerability Sanning with Nessus
Get it here
dpkg -i Nessus-10.2.0-ubuntu1110_amd64.debinstall it/bin/systemctl start nessusd.servicestart the serviceThen we go to https://127.0.0.1:8834/ to finish the install and configure it
If you are in the login page you can find out which username is installed with
/opt/nessus/sbin/nessuscli lsuserYou can then change your password with
/opt/nessus/sbin/nessuscli chpasswd usernameIf you are in the setup it is going to ask which version, you need to choose essentials (this version is free and will allow you to scan only private IP address) and then you will be able to register a user.
Here is and example of scan result (we ordered the vuln by severity by choosing disable groups in the settings wheel)
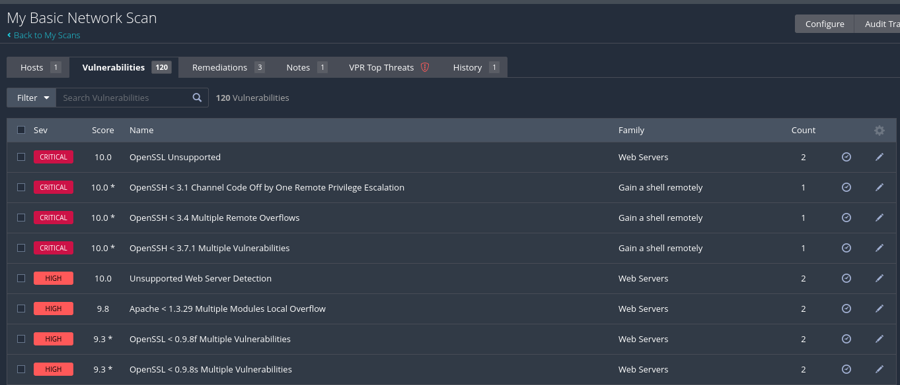
We can then check the vulns out and see if we can exploit them.
Default Credentials
If you stumble accross a login platform, first thing to try would be default creds. Here are some useful links for this
Weak Credentials
Possible paths after this step
Exploitation
The first we can jump into is the Exploitation stage. This happens when we do not yet have access to a system or application. Of course, this assumes that we have already identified at least one gap and prepared everything necessary to attempt to exploit it.
Post-Exploitation
The second way leads to the Post-Exploitation stage, where we escalate privileges on the target system. This assumes that we are already on the target system and can interact with it.
Lateral Movement
Our third option is the Lateral Movement stage, where we move from the already exploited system through the network and attack other systems. Again, this assumes that we are already on a target system and can interact with it. However, privilege escalation is not strictly necessary because interacting with the system already allows us to move further in the network under certain circumstances. Other times we will need to escalate privileges before moving laterally. Every assessment is different.
Information Gathering
The last option is returning to the Information Gathering stage when we do not have enough information on hand. Here we can dig deeper to find more information that will give us a more accurate view.
Source: Hackthebox Academy
Resources
General resources about enumeration
Last updated
