OWASP Top 10
SQL Injection



Defenses again SQLi

Broken authentication
Sensitive data exposure
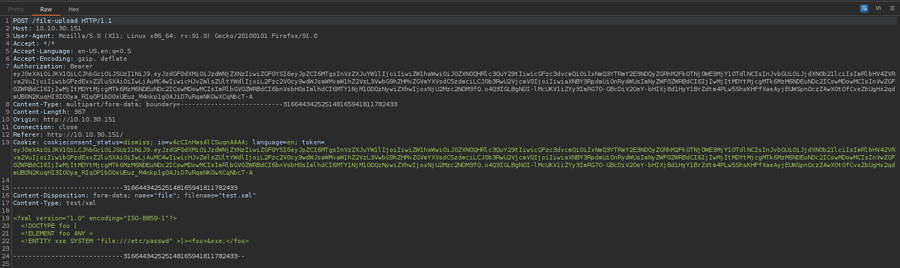
XML External Entities (XXE)
Broken Access Control
Security Misconfiguration
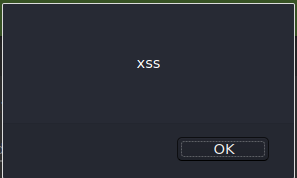
Cross Site Scripting
Reflected
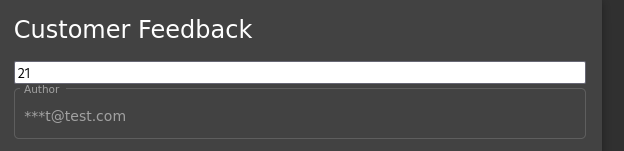
Stored
Prevent XSS

Insecure deserialization
Using components with known vulnerabilities
Insufficient Logging and Monitoring
Resources
Last updated