Setup your pentest lab
Virtualbox
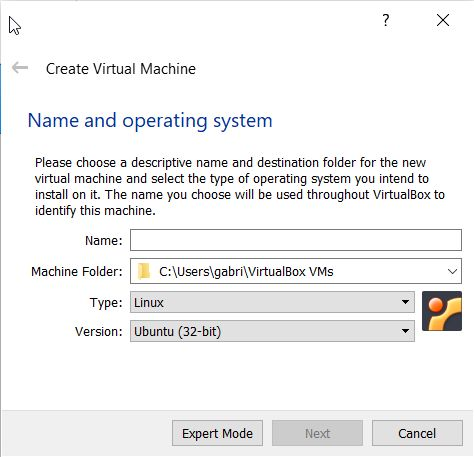
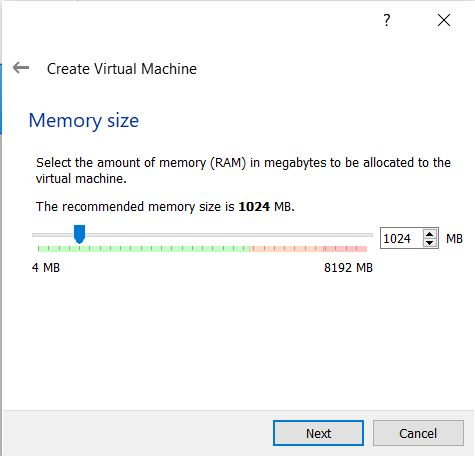
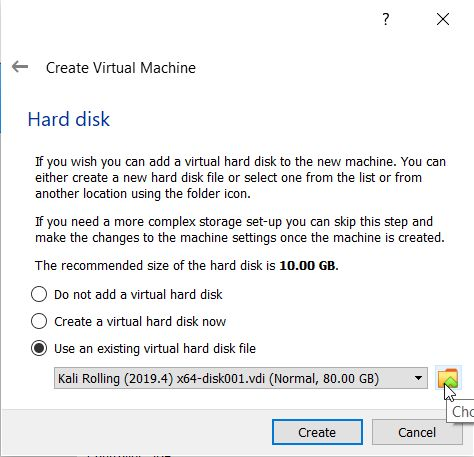
Create your virtual attacking machine with Kali Linux
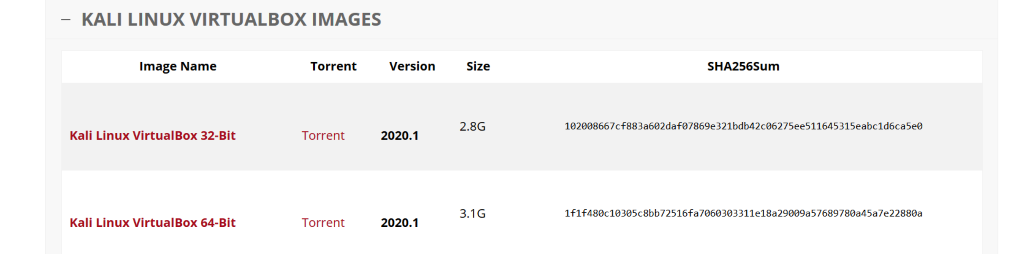
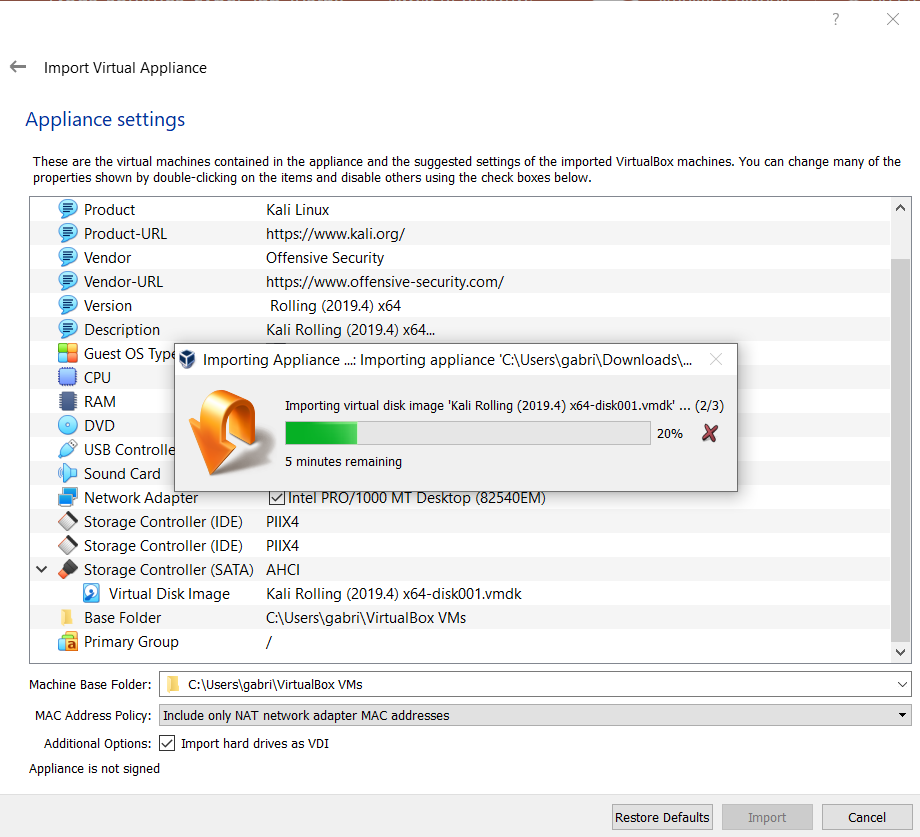
How to use vulnerable VM to practice
Where to find vulnerable machines
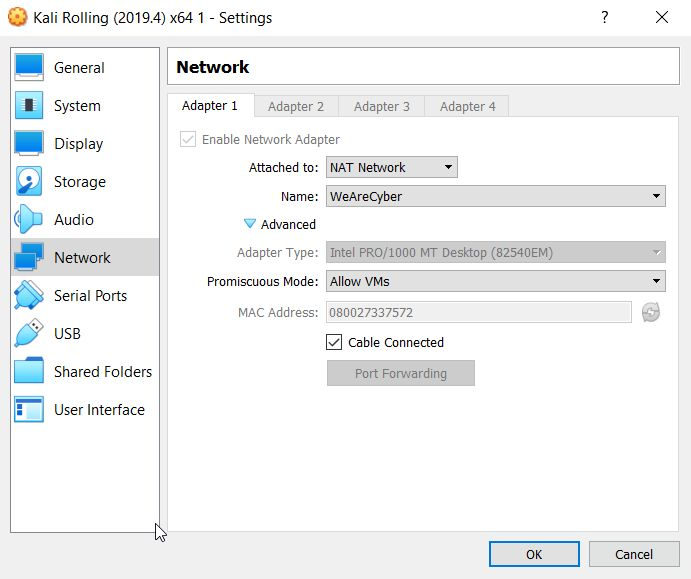
How to connect your kali with another machine
Install Metasploitable 2
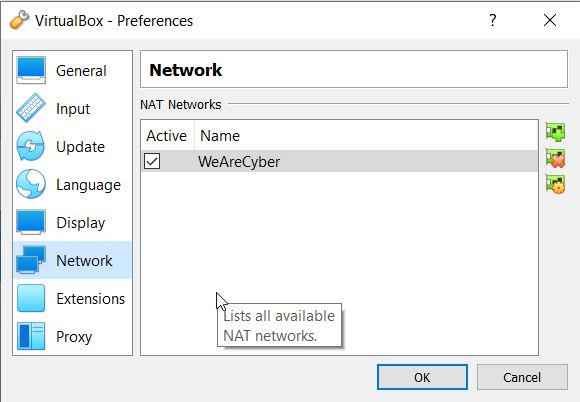
Connect Kali and Metasploitable 2 together
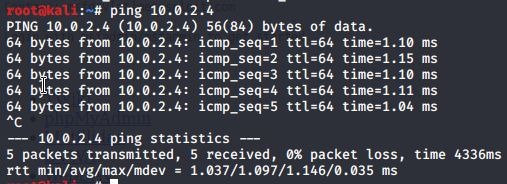
Check if our machines can communicate
Docker
Useful commands
AWS
Digital Ocean
COMING SOON

Resources
Alternative labs for general pentests
Labs for specific pentests
Thick Client
API
Android
Firewalls
Jenkins
SNMP
IDS IPS
Cloud
Tomcat
Memcached
Microsocks
Proxies
VOIP
SMTP
Routers
Active Directory
Last updated